Privileged access management: the key to strengthening your cyber defense
Data breaches are an ever-present threat in today's digital landscape. While many factors contribute to these incidents, one area plays a...
7 min read
 DriveLock
Aug 12, 2025 10:15:00 AM
DriveLock
Aug 12, 2025 10:15:00 AM

Cyber attacks are constantly evolving and becoming ever more sophisticated. It is therefore becoming increasingly important for companies, especially in the healthcare sector, manufacturing and critical infrastructures in Germany and Austria, to strengthen their own digital lines of defense. A key aspect of this is well thought-out access management.
| TABLE OF CONTENT |
Imagine if everyone in your company had a master key to all areas. That would be a huge security risk, wouldn't it? This is exactly where the least privilege principle comes in. It is a cornerstone of modern security strategies and ensures that every user and every system only receives the absolute minimum rights required to perform a specific task. No unnecessary authorizations, no superfluous risk.
In this article, you will find out what this fundamental principle is all about and why it is indispensable for you as an IT specialist in sensitive industries in order to effectively protect your systems from threats.
The principle of least privilege, often referred to as the principle of least privilege, is a fundamental security concept. It stipulates that each actor - be it a human user, a software program or a technical process - should only be granted the absolutely necessary access rights that it needs to perform its specific task. No more. This principle aims to minimize the potential impact of a compromised account or system.
To illustrate this, imagine a large company building: Instead of giving each individual employee a master key to all doors and rooms, everyone is only given the exact keys they need for their work area and specific tasks. An accounting employee does not need access to the server room, just as a production employee does not need access to personnel files. As soon as a task that temporarily required increased authorizations has been completed, these additional rights should be revoked immediately. This approach ensures that even in the event of a successful attack or human error, the damage is localized and the spread to critical systems is prevented.
In order to successfully implement the least privilege principle in your organization, it is essential to fully understand the different types of accounts and their specific authorization requirements. The application of the principle varies by account type to ensure that each entity has only the absolutely necessary rights.
Here are the three main categories of accounts you should consider when implementing the principle of least privilege:
Standard user accounts: These are the accounts used by the majority of your employees for day-to-day tasks. Their access rights are deliberately limited to the minimum required for basic activities such as sending emails, editing documents or accessing shared project files. These accounts should not have any authorizations for system configurations, software installations or access to sensitive administrative areas. The aim is to keep the attack surface as small as possible in the event of a possible compromise.
Privileged user accounts: These accounts are intended for IT staff and administrators who require extended access rights to manage, configure and maintain systems, applications and data. Examples include administrator accounts, database administrators, network technicians or DevOps engineers. In view of their far-reaching authorizations, these accounts are particularly worth protecting. Privileged Access Management (PAM) is often used here to strictly control, monitor and, if necessary, time-limit access.
Service accounts: These accounts are not used by people, but by software applications, processes and automated services to access network resources, databases or other systems. Here too, the consistent application of the least privilege principle is of the utmost importance: a service account should only receive the specific authorizations that are required for the smooth and secure operation of the associated application. An example would be a web server that only requires read access to a specific database table and no write or delete authorizations. Careful user management and regular review of these accounts is crucial to avoid security vulnerabilities.
Managing these different accounts and their permissions is often facilitated by Privileged Access Management (PAM) solutions, which ensure that privileged access is strictly controlled and monitored.
The consistent application of the least privilege principle is far more than just a recommendation; it is a fundamental necessity for the resilience of your IT security architecture. Especially in sensitive areas such as healthcare, manufacturing and critical infrastructures, ignoring this principle can have serious consequences. It forms a cornerstone that significantly strengthens your digital defense systems.
Reducing the attack surface: Any authorization that goes beyond what is absolutely necessary is a potential vulnerability. By limiting access rights to the absolute minimum, you significantly reduce the attack surface of your system. For example, if an attacker compromises a standard user account that only has basic rights, their ability to manipulate critical data, alter sensitive systems or steal wide-ranging information is severely limited. This drastically reduces the potential damage.
Containment of security breaches: Even with the best protective measures, a security breach can still occur. The least privilege principle acts as a crucial mechanism for damage limitation. If a privileged user account or a service account is successfully compromised, the principle prevents the attacker from spreading laterally through the network and accessing other, more privileged systems. The spread of the attack is contained, enabling faster detection and remediation and thus minimizing the overall damage.
Improved compliance and auditability: Numerous compliance regulations and industry-specific standards, such as the GDPR or healthcare requirements, demand strict control and verifiability of access rights. Implementing the least privilege principle not only helps you to meet these complex requirements, but also improves the auditability of your systems. With clearly defined and minimized permissions, you can more easily prove who has accessed which resources and when, which is invaluable during audits and in the event of a security incident.
Minimize human error: Unintentional errors by employees are a common cause of security incidents and data leaks. By limiting permissions to what is absolutely necessary, you reduce the risk of an employee accidentally changing critical system configurations, deleting sensitive data or accessing areas they are not authorized to access. Fewer rights mean fewer opportunities for unintentional misconfigurations or data exposure, which further increases the stability and security of your IT infrastructure.
The successful implementation of the least privilege principle is not a one-off project, but a dynamic and ongoing process. It requires careful planning, consistent execution and continuous adaptation to new circumstances. For companies looking to improve their existing cyber security, this principle provides a clear roadmap to optimize access rights throughout the system and thus significantly increase resilience to cyber threats.
Comprehensive inventory of all users and systems: Start with a detailed inventory. Create a complete list of all human users (employees, external service providers), all applications, services and automated processes that are active in your network. Also document all hardware and software components that require access to data or systems. This step forms the basis for a precise access management strategy.
Clearly define roles, tasks and required resources: For each identified entity - be it a standard user account, a privileged user account or a service account - analyze which specific tasks it performs and which data or systems are absolutely necessary for this. A precise role definition is crucial here. Define who needs what type of access (e.g. read, write, execute) to which resource.
Assign the minimum necessary authorizations: This is the core of the least privilege principle. Only grant authorizations according to the "need-to-know" and "need-to-do" principle. This means: always start with the least possible rights and only extend these if a specific task makes this unavoidable. Generally avoid granting extensive administrator rights where they are not absolutely necessary.
Regularly review and update authorizations: The digital landscape is constantly changing. Employees change roles, projects end, software is updated. The assigned access rights must therefore be reviewed and adjusted regularly - ideally on a quarterly basis or whenever there is a significant change. This is where user management plays a key role: ensure that outdated authorizations are revoked and new authorizations are assigned precisely. Automated processes can provide support here.
Implementation of monitoring and auditing mechanisms: A robust monitoring and logging system is essential to quickly identify unauthorized access or misuse of authorizations. Log all access activities and changes to authorizations. Security information and event management (SIEM) tools can help you analyze these logs and identify anomalies in real time. This is crucial to meet compliance requirements and ensure complete traceability in the event of a security incident.
Use of Privileged Access Management (PAM) solutions: Dedicated Privileged Access Management (PAM) solutions are invaluable, especially for privileged user accounts, which have the most far-reaching rights . These systems help you to centrally manage and monitor privileged access, record sessions and implement "just-in-time" access, where elevated rights are only granted for a limited time and for a specific purpose. PAM solutions significantly minimize the risk posed by these highly sensitive accounts.
By consistently implementing these steps, you create a robust security foundation that not only defends against current threats, but also prepares your organization for future challenges.
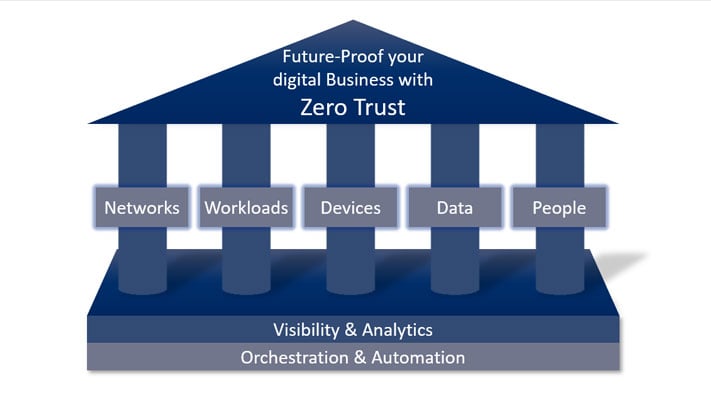
The principle of least privilege is a fundamental component of modern zero trust architecture. The Zero Trust model is based on the principle "Never Trust, Always Verify". In the context of the least privilege principle, this means that no user or device is trusted by default, even if it is within the corporate network. All access is explicitly authenticated and authorized based on the principle of least privilege. This combination creates a much more robust and resilient security environment that is ideal for meeting the challenges of today's cyber threats.
The principle of least privilege is not a one-off measure, but an ongoing commitment to security. By consistently applying this principle, you not only strengthen your defenses, but also create a more secure and resilient IT infrastructure for your business.

Data breaches are an ever-present threat in today's digital landscape. While many factors contribute to these incidents, one area plays a...

User management is a cornerstone of robust cybersecurity strategies. Whether you are an experienced IT professional in a critical sector such as...
The major strategic goal of cyber security in the digital age is to combat and mitigate data breaches. A company's data is its most valuable asset to...