7 principal pillars of Zero Trust Model
The major strategic goal of cyber security in the digital age is to combat and mitigate data breaches. A company's data is its most valuable asset to...
3 min read
 DriveLock
Jul 2, 2019 9:18:49 AM
DriveLock
Jul 2, 2019 9:18:49 AM

Enter the concept of "Zero Trust" in cybersecurity. It's not just a buzzword; it's a paradigm shift. Zero Trust challenges conventional wisdom and prompts organizations to rethink their security strategies from the ground up. In this blog post, we will embark on a journey into the heart of Zero Trust security.
| TABLE OF CONTENT |
Zero Trust is a comprehensive security architecture for businesses to prevent data breaches and defend against modern cybersecurity threats. Conventional security approaches often focus on external threats and its perimeters, leaving the organisation defenceless against insider threat. “Trust but verify” is no longer valid in the modern threat landscape as it leaves you vulnerable and ultimately reliant on crisis management.
Zero Trust, therefore, treats all devices, services and users with the same caution. This emphasises the focus on data and gathers security functions into a unified data protection strategy. You are now able to develop a strong defence and detection system with incident response capabilities to protect your business’ critical data.
Zero Trust emphasises the notion of “never trust, always verify”. This includes not trusting any user or device within and outside of your network. Well-equipped cybercriminals are consistently working to steal your sensitive data, the lifeline of your digital business. Zero Trust’s pragmatic and proactive approach attempts to overcome and stay ahead of the continuously growing and sophisticated cyber threat landscape.
The World Economic Forum’s 2019 Global Risks Report, rates cyber-attacks and data theft as the fourth biggest risk facing the global community. Recent incidents of data breaches in the APAC region occurred in March, whereby Toyota reported unwarranted access to its servers in Vietnam, Thailand, Japan and Australia. The most crucial attack breaching the data of 3.1 million of their clients in Japan. This sensitive information included the client’s names, addresses, birth dates and occupation among others.
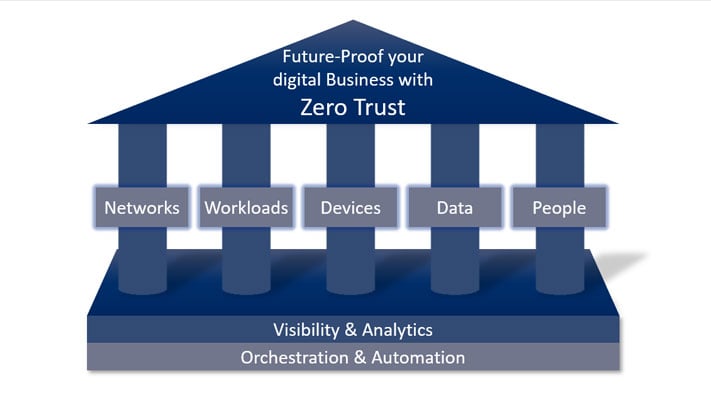
Within the zero trust security model, the following are critical elements, when it comes to protecting your business.
Securing data is the primary objective of Zero Trust. This is done by managing, categorising and encrypting data both at rest and in transit. All traffic must be checked and all user and services must be authenticated. Risk assessment in the context of Zero Trust assumes your business is already compromised and assesses the extent of the damage.
The proliferation of endpoints and specifically IoT devices have enabled significant vulnerability for networks and organisations. To secure devices with Zero Trust, you must control and secure every single device connected to your network.
In the current threat landscape, organisations underestimate and therefore fail to control how much power they give to their users. This includes your employees and partners. As the last line of defense in the Zero Trust approach enforces user authentication, it also protects user interaction.
DriveLock’s approach involves an integrated solution to implement holistic protection across your entire security architecture. DriveLock brings Zero Trust to the endpoint and enables a comprehensive Zero Trust security strategy:
With Encryption, we ensure that no data will leave in a readable format. In order to prevent the loss of data, DriveLock’s encryption software will monitor applications accessed by your employees. User authentication and authorised individual personnel passwords will be enforced.
You can centrally manage your BitLocker encrypted endpoints from a single management console. This also provides a Compliance Dashboard to view the encryption status of all machines within your organisation.
With DriveLock’s Device Control, only the authorised devices of authorised users are allowed access to company data. DriveLock's Application Control works in a similar manner. It includes whitelisting apps to assess potential risks involved when running the application.
Prevention Technologies are not perfect. If attackers manage to bypass the defense, they can go unnoticed for weeks and months. Our Analytics and Forensics module offers a monitoring system for you to track a security breach. DriveLock details which computer, which user and which app was breached. Automated reports will show you results within minutes of the incident.
DriveLock SmartCard Middleware and Virtual SmartCard support and enforce multi-factor authentication. Passwords are still one of the biggest weaknesses for IT security. Whether it is increasingly due to more realistic fraud and phishing mails or weak Passwords.
Smart SecurityEducation enables individuals in your company to develop their understanding of and guard against potential risks in order to effectively protect themselves and your business from cyber-attacks.
Cybersecurity has become more and more like an arms race. It’s not a matter of if, but when, there will be an incident.
By applying measures of Zero Trust to your organisation, you will benefit from:
The major strategic goal of cyber security in the digital age is to combat and mitigate data breaches. A company's data is its most valuable asset to...

Managing endpoint security can feel like a constant uphill battle. Keeping up with the latest threats, ensuring all devices are patched and...

TABLE OF CONTENT WHY TODAY'S IT SECURITY ARCHITECTURES SHOULD BE DESIGNED ACCORDING TO THE ZERO TRUST MODEL WHAT USED TO WORK DOES NOT...