Log4j has been the talk of the town for several weeks now. We have also already commented on this in a detailed post blog about Log4j and Log4Shell.
There are many descriptions of the vulnerability and its criticality on the Internet (CVE-2021-44228 in Apache Log4j 2). Nevertheless, many IT departments are already challenged by the simple question: "Am I affected at all, and if so, on which systems and in which application?"
There is a compilation of the affected applications on Github, for example. But do companies actually use them?
Even if the IT department has appropriate asset management, so-called shadow IT is left out of the picture here.
This can be remedied by comprehensive vulnerability scanning, offered by DriveLock for end devices. (Watch the webcast about it on the right). This allows you to scan all systems with little effort and provides you with clarity as to which application may require any action.
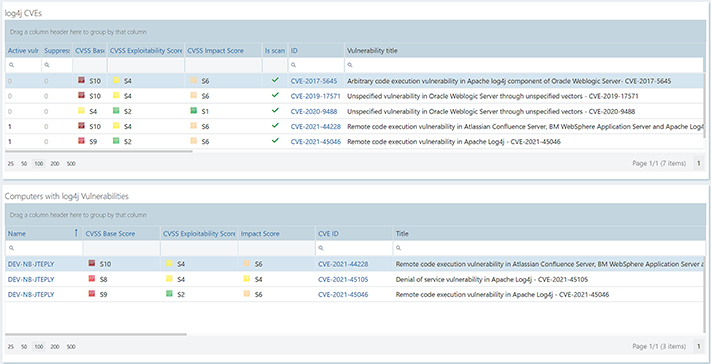
For the users of our DriveLock Vulnerability Management, we have built a simple and clear dashboard that bundles the relevant information around Log4j.
FIND OUT MORE ABOUT VULNERABILITY MANAGEMENT FROM OUR BLOG POST!
DriveLock Vulnerability Management Dashboard
1. In the DriveLock Operations Center, select "Add new dashboard tab".
2. In the pop-up window for creating a dashboard, select "New dashboard from string". Then copy the string below into the input field.
{"dataCrc":3377563328,"data":{"type":4,"content":{"rows":[{"id":"02E8F511-406A-4050-A333-3E21DF98833E","factor":2,"index":0,"widgets":[{"id":"CDBB0FAC-FB67-4CBC-8014-1710DFB7CAC0","displayName":"log4j CVEs","factor":1,"index":0,"templateId":"7C6B1F72-10F2-4514-A213-10113D3AFB1E","type":"List","query":"and(contains(description,log4j),eq(isScanable,true))","timespan":null,"groupBy":null,"styleClass":null,"serviceTag":"VulnerabilityCveView","options":{"columns":["activeAffectedComputerCount","supressedAffectedComputerCount","cvssBaseScore","cvssExploitabilityScore","cvssImpactScore","isScanable","id","vulnerabilityTitle","vulnerabilityDescription"],"sortBy":null,"highRange":{},"lowRange":{},"category":1,"icon":"dl-user-monitor","color":"rgba(91,112,139,1)"},"isCustomWidget":true}]},{"id":"2E6BC1EB-6D2B-4C9C-A602-E223D3012D28","factor":2,"index":1,"widgets":[{"id":"2B6557B3-AC26-46B6-89B3-6D05DB69E62C","displayName":"Computers with log4j Vulnerabilities","factor":1,"index":0,"templateId":"B43B8BA3-C80C-4EF0-BD26-7B04EA2B3316","type":"List","query":"and(eq(status,1),contains(vulnerability.description,log4j),or(eq(isSuppressed,__NULL__),eq(isSuppressed,false)))","timespan":null,"groupBy":null,"styleClass":null,"serviceTag":"ComputerVulnerabilityView","options":{"columns":["computer.name","baseScore","exploitabilityScore","impactScore","vulnerability.cveID","vulnerability.title","detectedAt","vulnerability.description"],"sortBy":["computer.name"],"highRange":{},"lowRange":{},"category":3,"icon":"dl-user-monitor","color":"rgba(91,112,139,1)","activateLabels":true,"activateLabelConnector":true,"activateLegend":true,"legendPosition":"right","showTop":0},"isCustomWidget":true}]}],"sortIndex":11,"userId":"C2615E5A-389C-4C0D-AD9B-0B3D18FC13B0","name":"log4j","id":"EC5BC841-D1D3-429A-B4DD-32A94F25FFBF","isReport":false},"templates":[{"id":"7C6B1F72-10F2-4514-A213-10113D3AFB1E","displayName":"log4j CVEs","widthFactor":1,"factor":1,"type":"List","query":"and(contains(description,log4j))","timespan":null,"groupBy":null,"description":"log4j CVE overview","styleClass":null,"styleMapper":null,"serviceTag":"VulnerabilityCveView","options":{"columns":["activeAffectedComputerCount","cveLastModifiedDate","cvePublishedDate","cvssBaseScore","cvssExploitabilityScore","cvssImpactScore","cvssVector","cvssVersion","description","id","isScanable","isSuppressed","lastChange","ovalItemID","severity","supressedAffectedComputerCount","updateCounter","vulnerabilityDescription","vulnerabilityId","vulnerabilityTitle"],"sortBy":null,"highRange":{},"lowRange":{},"category":1,"icon":"dl-user-monitor","color":"rgba(91,112,139,1)"},"isCustomWidget":true,"isInternalWidget":false,"isPrivateWidget":false,"ownerId":null,"requiredFeatures":null,"sortIndex":30,"newFontIcon":"dl-table","displayNameResolved":"log4j CVEs"},{"id":"B43B8BA3-C80C-4EF0-BD26-7B04EA2B3316","displayName":"Vulnerability List","widthFactor":1,"factor":1,"type":"List","query":"and(and(eq(status,1),or(eq(isSuppressed,__NULL__),eq(isSuppressed,false)),or(eq(isVulnerabilitySuppressed,__NULL__),eq(isVulnerabilitySuppressed,false))))","timespan":null,"groupBy":null,"description":"","styleClass":null,"styleMapper":null,"serviceTag":"ComputerVulnerabilityView","options":{"columns":["computer.name","baseScore","exploitabilityScore","impactScore","vulnerability.cveID","vulnerability.title","detectedAt"],"sortBy":["computer.name"],"highRange":{},"lowRange":{},"category":3,"icon":"dl-user-monitor","color":"rgba(91,112,139,1)"},"isCustomWidget":true,"isInternalWidget":false,"isPrivateWidget":false,"ownerId":null,"requiredFeatures":null,"sortIndex":30,"newFontIcon":"dl-table","displayNameResolved":"Vulnerability List"}],"version":1}}
This gives you a dashboard that shows the relevant vulnerabilities in the upper section and the affected machines in the lower section.
We will be happy to answer any questions you may have about DriveLock Vulnerability Management!
 DriveLock
Jan 13, 2022 2:33:08 PM
DriveLock
Jan 13, 2022 2:33:08 PM




.png)