Video
How can data, devices and systems be effectively protected according to the Zero Trust model?
With the Zero Trust model, a sophisticated security strategy becomes a reality in your business.
In the highly digitalized business, it's critical to effectively protect your most valuable assets: Your data. Risks from data theft, data misuse, data loss or data corruption are unacceptable. The Zero Trust model helps to implement a sophisticated security strategy for maximum security and prevention in business - no matter where, on which endpoint and for all data throughout the complete lifecycle.
Traditional security has had its day. The traditional approach that provided security for a long time can no longer adequately protect companies today. The current digitalization goes far beyond the former boundaries of the core business. Potential dangers from data misuse and cybercrime are exacerbating the situation. What is needed is a new, modern and adapted security concept that directly contributes to a company's security strategy: Zero Trust.
Traditional security concepts assume that everything within the corporate network is benign. Anything coming from outside, on the other hand, is potentially dangerous and therefore in need of inspection. However, modern business environments have completely different structures. Networking with other companies, the home office, intensive use of the cloud, and the Internet of Things mean that traditional network boundaries are largely disappearing. So what then is still good or bad?
The time is ripe to choose the paradigm shift toward data-centric zero trust security. What does this mean? That basically everything on the network is off-limits until dedicated permission is granted. There is no distinction between inside and outside the corporate network. All endpoints, devices, users or applications are distrusted. Access to networks and data is only granted if users, endpoints and applications are allowed access to precisely the resources they need at maximum.
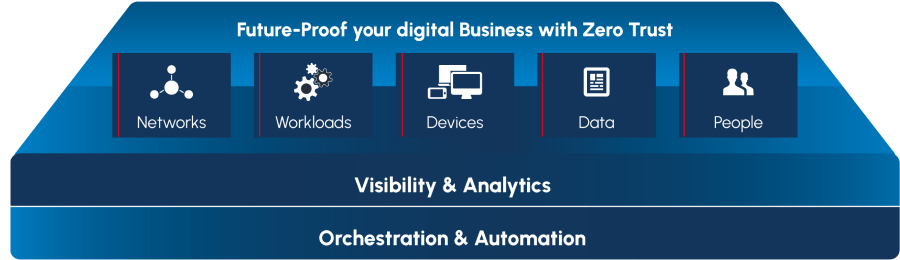
Zero Trust has the ability to granularly segment, isolate and control the network. This ensures that only certain users, applications or devices with specific requirements can access sensitive network segments or microperimeters.
Zero Trust ensures throughout the application stack that connections, applications and components are fundamentally treated as threat vectors and must be equipped with Zero Trust controls and technologies. Of highest importance are workloads to the public cloud.
Zero Trust controls all devices on the network and is able to isolate and secure all devices and computers at all times. IoT and network-based device technologies, in particular, have enormous potential to compromise networks and enterprises due to the frequent lack of embedded security mechanisms.
Zero Trust ensures data security. Securing and managing data, categorizing and developing classification schemes, and encrypting both at rest and in transit are key components of the Zero Trust principle.
Zero Trust controls all known and unknown applications and regulates network traffic and data access according to the "never trust, always verify" principle. This means that applications that do not have verified and dedicated permission have no chance of causing damage to the network or data.
Zero Trust prevents the user from becoming a risk. The strategy is to limit movement on the network and data access rights to an absolute minimum. Only what a known and verified user with a dedicated application needs to access the network and resources is allowed.
Zero Trust creates visibility and transparency. This gives security experts a complete overview of all networks, segments, microsegments and data resources. They also have an overview of who is accessing or attempting to access resources (without authorization), when and via which path. Zero Trust ensures this visibility and transparency across all instances - from internal resources to the cloud.
Zero Trust enables enterprise-wide automation and orchestration of the entire security infrastructure. Seamless integration of the leading Zero Trust model with other complementary solutions creates an ecosystem in which critical information about security status is shared. This enables far-reaching automation, for example to ensure a fast and effective response to potential threats.

Listen to our video to learn how the strategic DriveLock Zero Trust Platform can help you protect your valuable data, devices and systems more effectively than ever.
Is your company building on modern digital infrastructures? Do you work with a variety of different networked devices and applications? Do you use the cloud and are externally networked with various services and users? Then DriveLock has the right security platform for you. With the DriveLock Zero Trust Platform, we provide the security you need to run a successful business with minimal risk.
Every single DriveLock security solution, as well as third-party security solutions like Microsoft, integrate seamlessly with our Zero Trust Platform. We protect your enterprise data, devices and systems, no matter what operating system platform - on-premise or in the cloud. The DriveLock Zero Trust Platform combines Data Protection, Endpoint Protection, Risk & Compliance and Identity & Access Management into one security ecosystem for the protection you need in your business today and in the future.
Our team of experts is at your side with experience and proven expertise. We support you in the paradigm shift from traditional security to the zero trust model. We are your pioneer and companion for a security that meets the requirements of your digital business.
Maximum data security with the DriveLock Zero Trust Platform
How can data, devices and systems be effectively protected according to the Zero Trust model?
News, Blogs, Whitepapers and Webinars about IT Security! Protect your endpoints with reknown Security Solutions by DriveLock.
Sign up here for the DriveLock News Service: