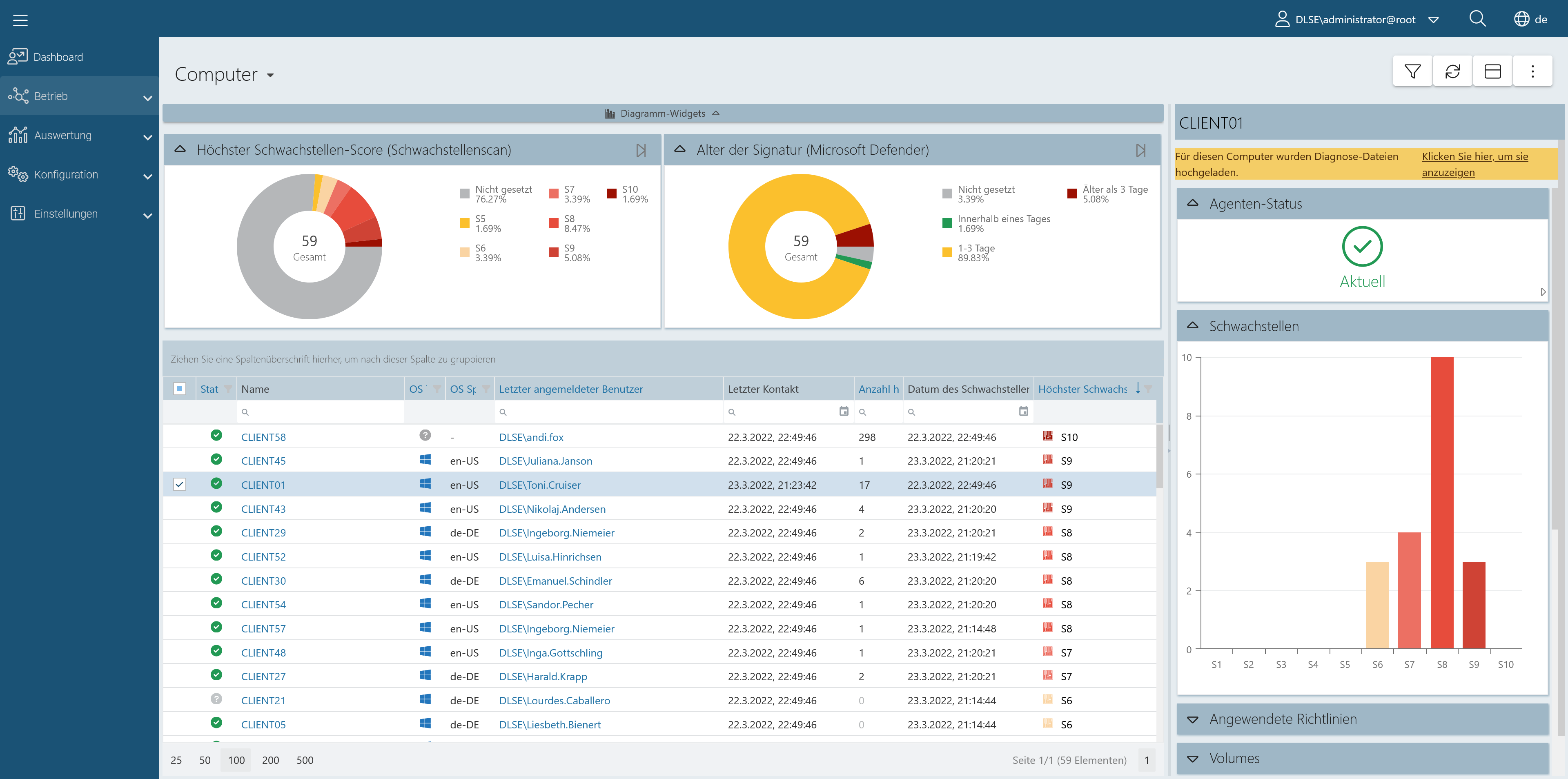
Dashboard, widgets and specific views in DriveLock Operation Center
DriveLock Vulnerability Management
Protection and compliance for your business thanks to automated identification and remediation of vulnerabilities
Challenges
Attackers often exploit both known (old) and unknown (zero day) vulnerabilities or weaknesses in software to gain control of computer systems, steal sensitive information, and cause damage. IT managers need to identify and control the risks associated with these vulnerabilities.- You want to prevent your systems from being compromised by exploiting any potential vulnerability.
- You need an automated solution that scans for vulnerabilities and proactively addresses (closes or mitigates) any discovered flaws.
- You want to keep track of changes to your attack surface at all times.
- You need a solution that can automatically prioritize vulnerabilities.
Find out more about Vulnerability Management!
Our Solutions
Identify vulnerabilities on your endpoints and prevent potential malware attacks with DriveLock Vulnerability Management
- Find missing patches, outdated software programs, or libraries with known vulnerabilities - on a scheduled, ad-hoc, or regular basis.
- Reduce your cyber risk by continuously assessing your security and compliance posture.
- Discover and prioritize unknown assets and vulnerabilities.
- Identify and assess discovered vulnerabilities directly in DriveLock Operations Center.
- Reduce costs, increase efficiency and strengthen your cybersecurity through automation.
Advantages with DriveLock Vulnerability Management
Identify and control the risks associated with vulnerabilities
Multi-tenancy, multi-user and role-based access
Vulnerability database with 115,000 definitions for approximately 140,000 CVES, updated hourly
Internationally accepted classification standard, validated solution
Functionality
How DriveLock Vulnerability Management works:
As part of the DriveLock Zero Trust Platform, DriveLock Vulnerability Management provides a comprehensive view of your infrastructure, reveals your attack surface, and enables you to manage and measure your cyber risk.

NO OBLIGATION, NO COMMITMENT.
Free 30-day trial without obligation
See for yourself. Test the usage scenarios relevant to your company.
Test today - Be HYPERSECURE tomorrow!
NO OBLIGATION, NO COMMITMENT.
Free 30-day trial without obligation
See for yourself. Test the usage scenarios relevant to your company.
Test today - Be HYPERSECURE tomorrow!
Further Product Information
In your preferred format. As audio, video, PDF or in a personal conversation.
Flyer
In the product PDF you will find a detailed overview of the benefits and practical use cases of our solution.
Whitepaper
Download our topics and solution-relevant whitepapers free of charge and gather more knowledge about DriveLock
Blog
Find out everything you need to know about a vulnerability mangement in the companies from our blog post.
Here you will find related topics
Mutual Respect is an important ingredient that makes the partnership between UBM GmbH and DriveLock SE special. Mutual support and cooperation make the partnership work flawlessly.
DriveLock, a highly respected German Cyber Security Firm, develops its solutions to meet and exceed both current and future Industry demands. Partnering with DriveLock is the result of our increasing need for effective and future-proof cybersecurity, which our customers in turn expect from LargeNet.
We deliver an important area of IT security. DriveLock delivers German built quality products and solutions. This provides us with the confidence we need, especilly in times of the DSGVO.
BIM is a leading Swiss IT engineering company delivering meaningful digitalization with IT solutions. Our solutions fulfill one or more of these goals: The solution either makes money, saves money and mitigates risks. Innovative and quality-obsessed vendors like DriveLock are part of our secure digital transformation ecosystem, and are critical in helping us meet our solution goals.
We love DriveLock for the exceptional control and security it provides. It has significantly enhanced our data protection and reduced 99.9% of previously encountered USB storage-based malware. DriveLock gives us peace of mind, knowing our sensitive information is safeguarded better.



















.png?width=500&height=200&name=DsiN%20Mitglied%20%20(500%20x%20200%20px).png)





