DriveLock Endpoint Detection & Response
Start your test now!
Category: Use Case
Module: Endpoint Detection & Response
Testing Time: 30 min
In this use case, we will show you how DriveLock Detection & Response works.
1. What is this use case about?
While preventative measures play an important role in making an organization more resilient to attacks, detection capabilities are critical to identifying ongoing attacks that may have escaped prevention mechanisms.
Without Endpoint Detection & Response (EDR) capabilities, the reliability of prevention mechanisms is the only thing you can count on. Some argue that 100% protection is impractical, even impossible, and that existing blocking and prevention capabilities are inadequate. Instead, it should be possible to find out what is happening on the end device. Comprehensive protection requires an adaptive process for prediction, prevention, detection and response in order to react appropriately to security breaches. What happens to the one percent that make it through? If attackers manage to evade defenses, they can go undetected for weeks or even months. This period of “silent failure” means success for the attackers and potential disaster for the company.
Threat detection and response are becoming increasingly important, enabling organizations to survive an attack when other controls fail. EPP (Endpoint Protection) and EDR are growing together in an EDR platform.
2. How does it affect your client computer?
When this use case is applied to your computer, event filters and application monitoring are used in addition to the events collected by DriveLock. The entire definition of the filter and application authorization is based on the MITRE ATT&CK framework.
This sample policy contains configurations for the following MITRE ATT@CK tactics:
- Account Discovery (T1087)
- Account Manipulation (T1098)
- Brute Force (T1110)
- Create Account (T1136)
- Create or Modify System Process (T1543)
- Domain Trust Discovery (T1482)
- Hardware Additions (T1200)
- Indicator Removal on Host (T1070)
- Masquerading (T1036)
- Signed Binary Proxy Execution (T1218)
- System Network Configuration Discovery (T1016)
- System Network Connections Discovery (T1049)
- System Owner/User Discovery (T1033)
- Use Alternate Authentication Material (1550)
- Valid Accounts (T1078)
These tactics mentioned generate alerts or trigger partially automated responses on the end device. The responses include:
- Delete-File
- Delete-LocalUser
- Disable-LocalUser
- Disable-NetworkAdapters
- Kill-Process
- Remove-LocalGroupMembers
- SetDriveLockPBAOptions
- Set-RegKey
- Shutdown-Computer
3. Example of an alert with a response
The “Local account creation” alert with the corresponding response allows you to run through the MITRE technique https://attack.mitre.org/techniques/T1136/001/ as an example.
Once the policy has been assigned, create a new local user.
The user should be removed again after a short time. The following response script takes care of this:
This is linked to the alert as a response.
4. How to monitor the results in the DOC?
The results of the EDR use case are displayed in the Threats > Alerts workspace.
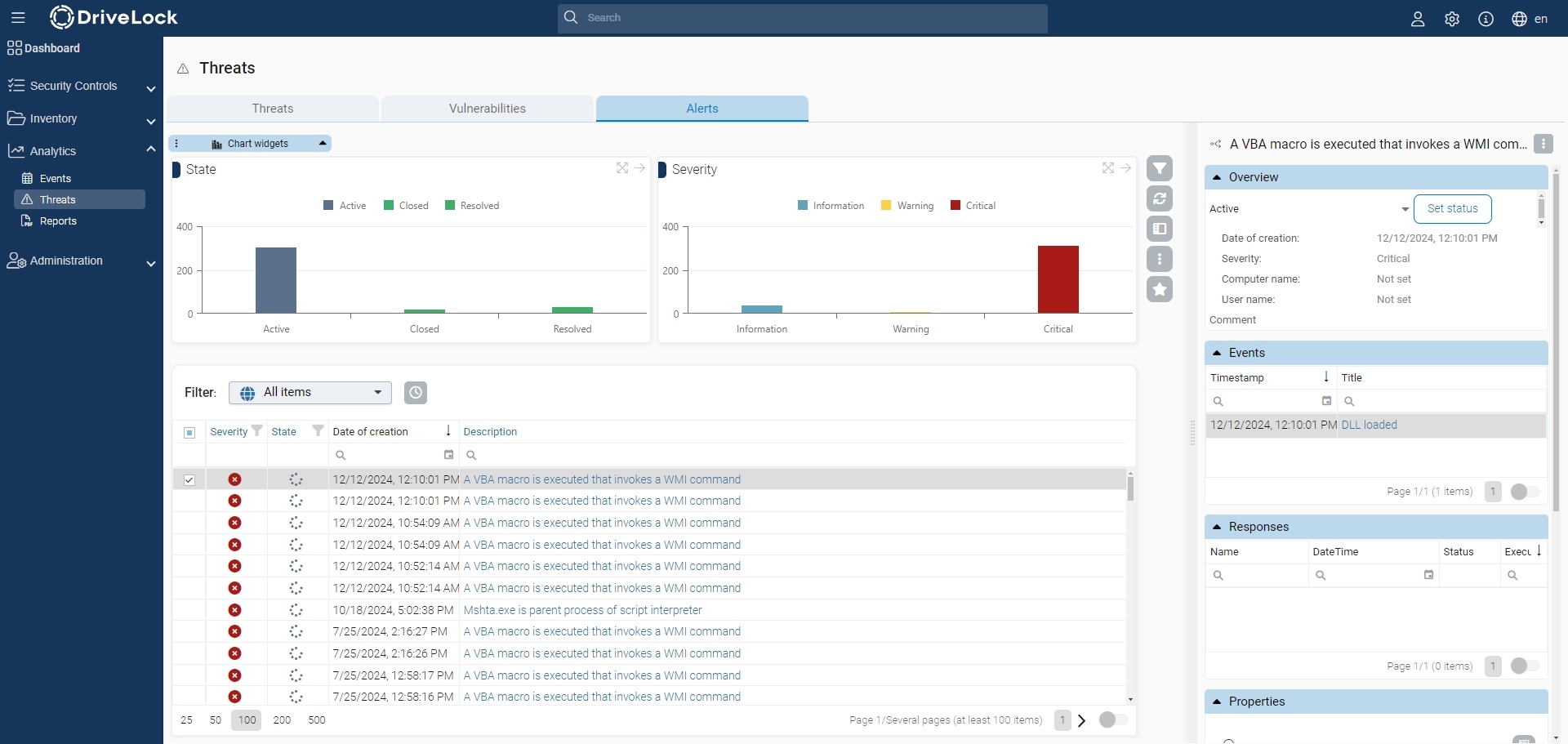
In this workbench, you can view all triggered alarms and their status. You can also find all the details in the event views.
5. Further EDR examples
In the 90 Detection & Response policy, you will find further alerts under Alert definitions. If you open the properties of an alert, you will find a description with a link as well as the conditions and responses defined under Event filter definitions and Response definitions.




