DriveLock Vulnerability Scanner
Start your test now!
Category: Use Case
Module: Vulnerability Scanner
Testing Time: 30 min
This use case shows you how the DriveLock Vulnerability Scan searches for known and unknown vulnerabilities.
1. What is this use case about?
DriveLock Vulnerability Scan automatically and regularly scans your computer system for known Windows vulnerabilities. In doing so, we access a database that is updated several times a day. The results found are then displayed in the DriveLock Operations Center in a separate view, with an assessment of the impact and risk. So are missing patches, outdated software programs or libraries with known vulnerabilities. This allows security teams to evaluate the level of security more accurately in the organization and set automatic alerts based on the assessments.
2. How does it affect your client computer?
On your test devices with an active DriveLock agent, vulnerabilities are scanned once a week after the Activate Vulnerability Management group has been assigned. Results are sent to the DriveLock Enterprise Service and can be viewed in the DOC.
Note: Depending on the performance of your test machine and the amount of software installed on it, the vulnerability scan can take up to 3 hours.
3. How to monitor the results in the DOC?
The results of the vulnerability scan are available in the DOC both in a separate dashboard and in the Security controls > Vulnerabilities view.
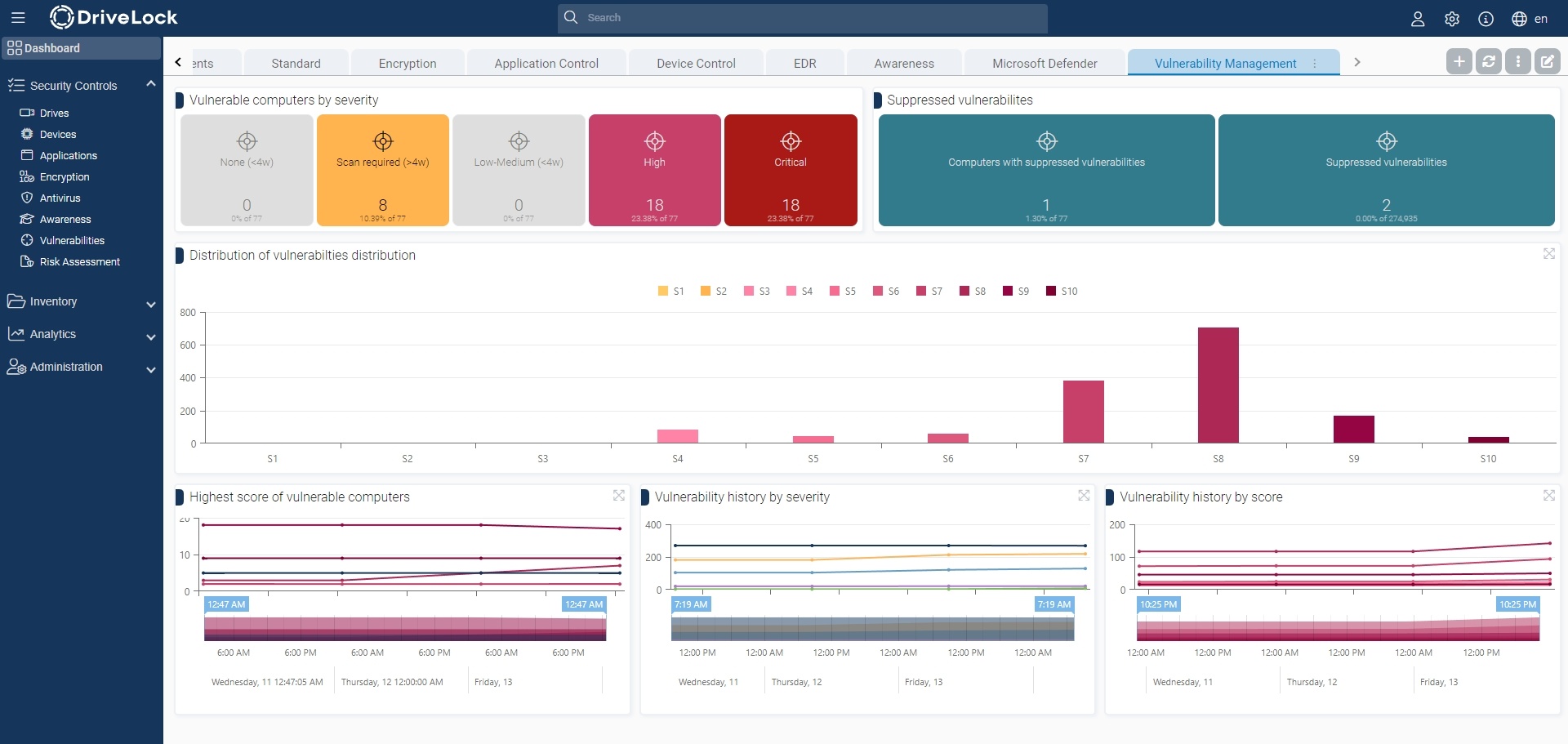
Vulnerable computers can be identified with an assessment of the risk and impact so that you can take appropriate action, such as applying missing patches or updating software.
The Common Vulnerability Scoring System is used to indicate the criticality of a vulnerability. The base score indicates the criticality of a vulnerability. This is in a range from S1 (non-critical) to S10 (highest criticality).
Various tabs are available in the vulnerability view:
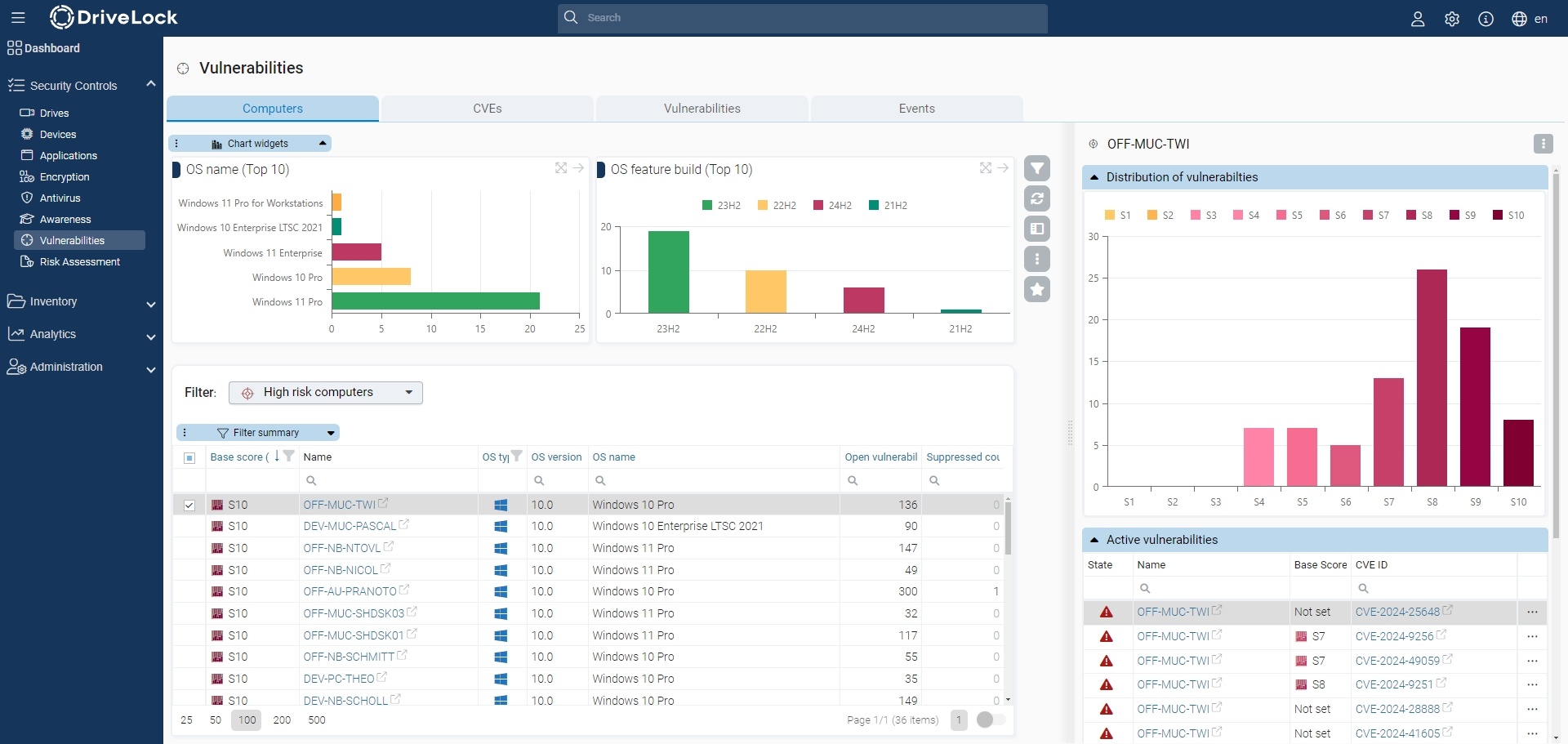
- Computer (computer overview)
Shows the open or suppressed vulnerabilities for a computer
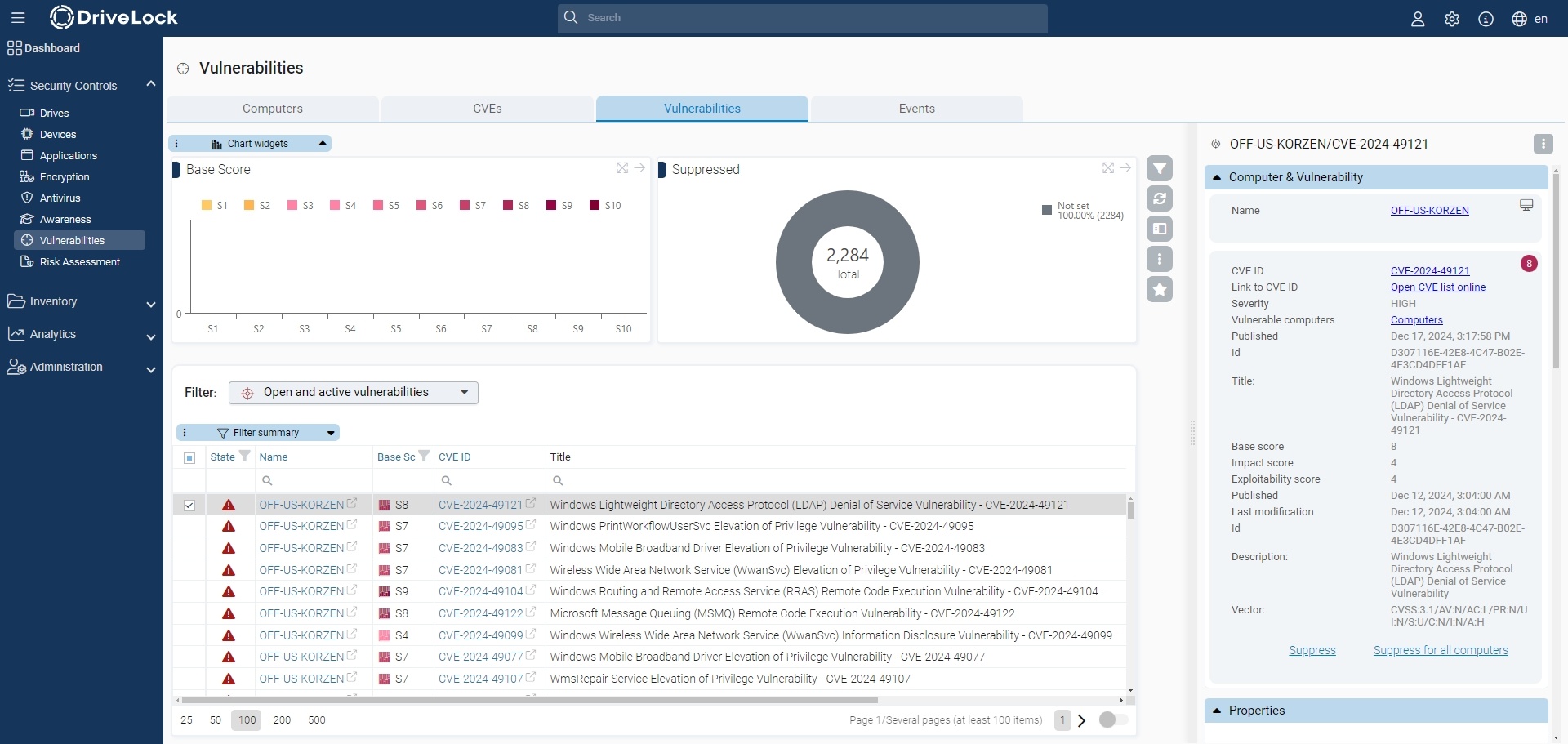
Allows you to suppress the vulnerability for one or all computers - CVEs (Common Vulnerabilities and Exposures (CVE®))
Shows which CVEs exist
-> Allows suppression for all computers
Shows the computers at risk in the detailed view of a CVE
-> Allows navigation to the vulnerable computers (opens the list of detected vulnerabilities) - Vulnerabilities (vulnerability overview)
Shows for a computer when a specific vulnerability was detected
Allows suppression for one or all computers - Events
Shows all events related to vulnerability management. The following list shows possible vulnerability events.
| 690 | Information | Vulnerability scan successful | Vulnerability scan was successfully run and results uploaded. DES server: [DES name] ; connection ID: [object ID]. |
| 691 | Error | Vulnerability catalog not downloaded | Vulnerability scan could not be executed because the vulnerability catalog has not been downloaded from the server yet |
| 692 | Error | Vulnerability scan failed | The scan failed during the vulnerability scan. Error: [ErrorMessage] |
| 693 | Error | Error at the start of a scan | Error when starting a vulnerability scan. Error code: [ErrorCode]; Error: [ErrorMessage] |
| 694 | Error | Failed to download the vulnerability catalog |
Error downloading vulnerability catalog. |
| 695 | Error | Create incident Vulnerability scan failed |
Error creating vulnerability scan event. Step: [StepName]; ErrorCode: [ErrorCode]; Error: [ErrorMessage] |


