DriveLock Device Control
Start your test now!
Category: Use Case
Module: Device Control
Testing time: 30 min
This use case, will show you how easy it is to protect your endpoints with DriveLock Device Control.
1. What is the use case about?
DriveLock provides intelligent device control, with or without cloud services. USB flash drives continue to be an important means of exchanging data. To protect sensitive information from ending up in the wrong hands, DriveLock monitors transactions performed via USB storage devices. In case you have to use a USB flash drive to store such data, you can encrypt it with DriveLock. Staff also use company USB ports to charge cell phones or other devices. This allows malware to quickly enter devices and systems.
Survey shows that 80 % of employees have already copied data from or to USB flash drive or connected devices to the USB port for charging without even considering the consequences. DriveLock protects your business effectively. Threats like Meltdown or Spectre reveal the need for more than just sophisticated permissions, antivirus software and firewalls.
This use case is aimed at protecting your test computers in terms of devices. Device control is configured in a very simple but effective way. Additionally, DriveLock monitors and checks each connection and date flow. This provides you with all the necessary information you need for your compliance reporting or for forensics in case of a data breach.
2. How does it affect your client computer?
This how-to video shows you how to assign the policy:
After you have assigned the Activate Device Control group to a computer, the 10 Device Control policy is active on the computer. All drives are locked except of internal and encrypted hard disks as well as network drives. Smartphones such as Apple, Android or BlackBerry devices are also locked.
Details on lock settings are explained in the following video:
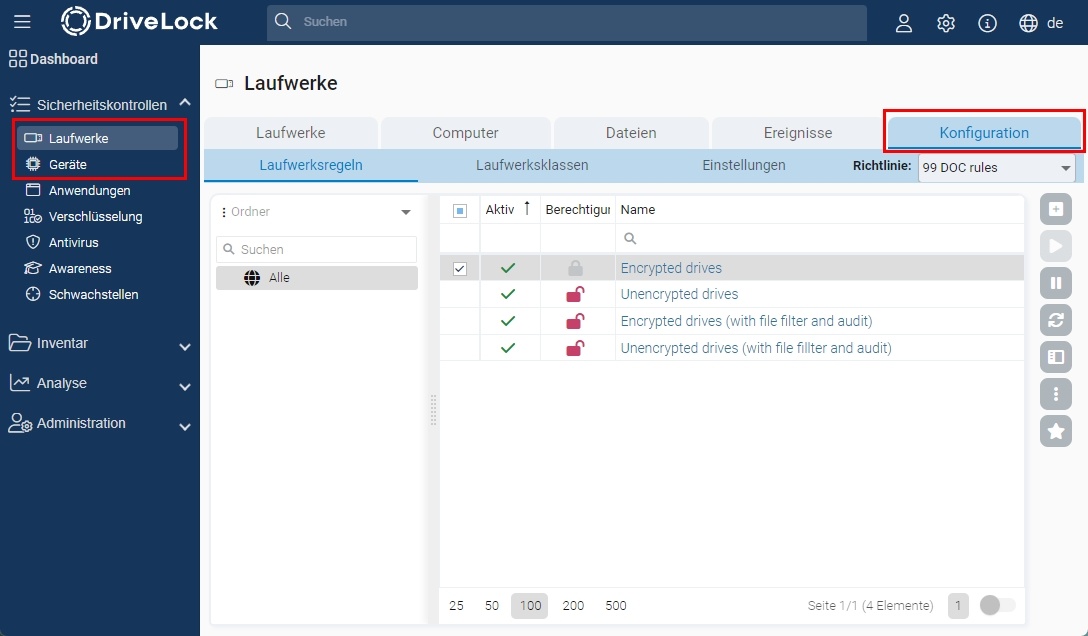
To use a drive like a USB drive, you must add it to a drive rule. To do this, simply connect the drive to the client. Inventory data of the drive is now collected, which can be found in the DriveLock Operations Center (DOC) under Security Controls > Drives.
In the Configuration tab, select one of the drive rules and click on the “+” symbol on the right-hand side. You can now select the inventoried drive or add it using one of the other options.
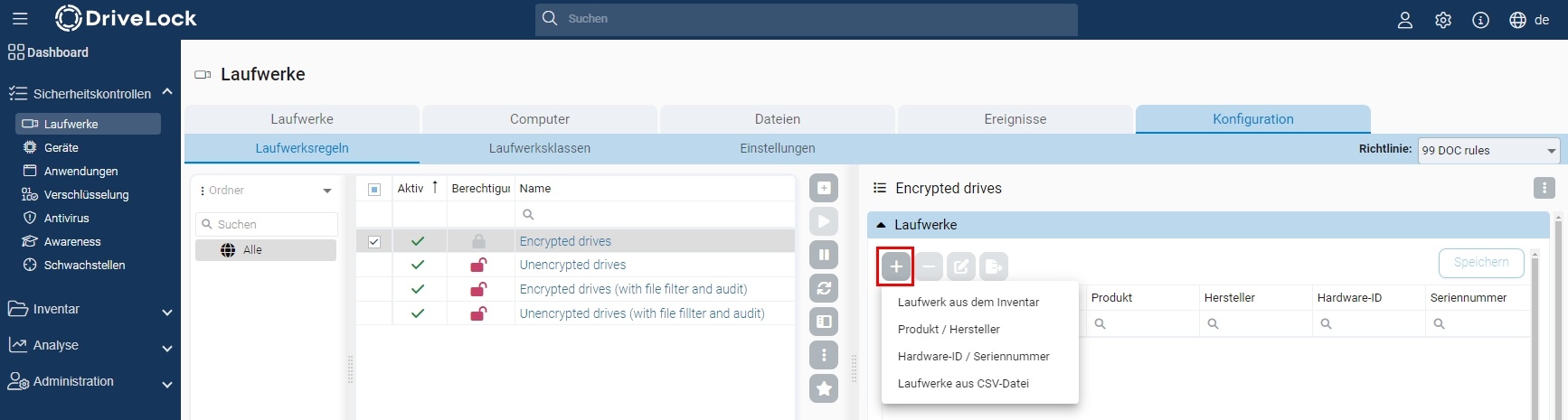
Alternative: Right-click on the drive in the Drives view to add it to a drive rule or create a new rule. Now this drive can be used on computers with DriveLock Device Control.
The following preconfigured drive rules are available in the demo environment:
- Encrypted drives: Drives that are added to this rule must be encrypted in order to access them (see the following chapter Exception: Forced encryption).
- Unencrypted drives: Drives that are added to this rule can also be used directly without encryption.
- Encrypted drives (with file filter and audit): Similar to the Encrypted drives rule, but with additional file filtering and auditing. All file types are permitted by default.
- Unencrypted drives (with file fillter and audit): Similar to the Unencrypted drives rule, but with additional file filtering and auditing. All file types are permitted by default.
Like drives, you can also unlock devices by adding them to a device rule via Security Controls > Devices.
The following device rule is already preconfigured:
Allowed devices: Devices added to this rule can be used directly.
Drive and device events will be audited by the DriveLock agent and can be monitored in the DOC.
The drive and device rules can be found in the Configuration tab (Security Controls > Drives > Configuration or Security Controls > Devices > Configuration), where drives and devices can also be removed.
Exception: Forced encryption
Watch this video for details on enforced encryption:
USB drives that you have added to a drive rule with Enforced Encryption option can be used, if they are encrypted. If they are not, a wizard will appear that will allow you to encrypt the USB drive.
With the Device Control policy, DriveLock provides the following encryption solutions for removable media: DriveLock Encryption 2-Go and Microsoft BitLocker To Go.
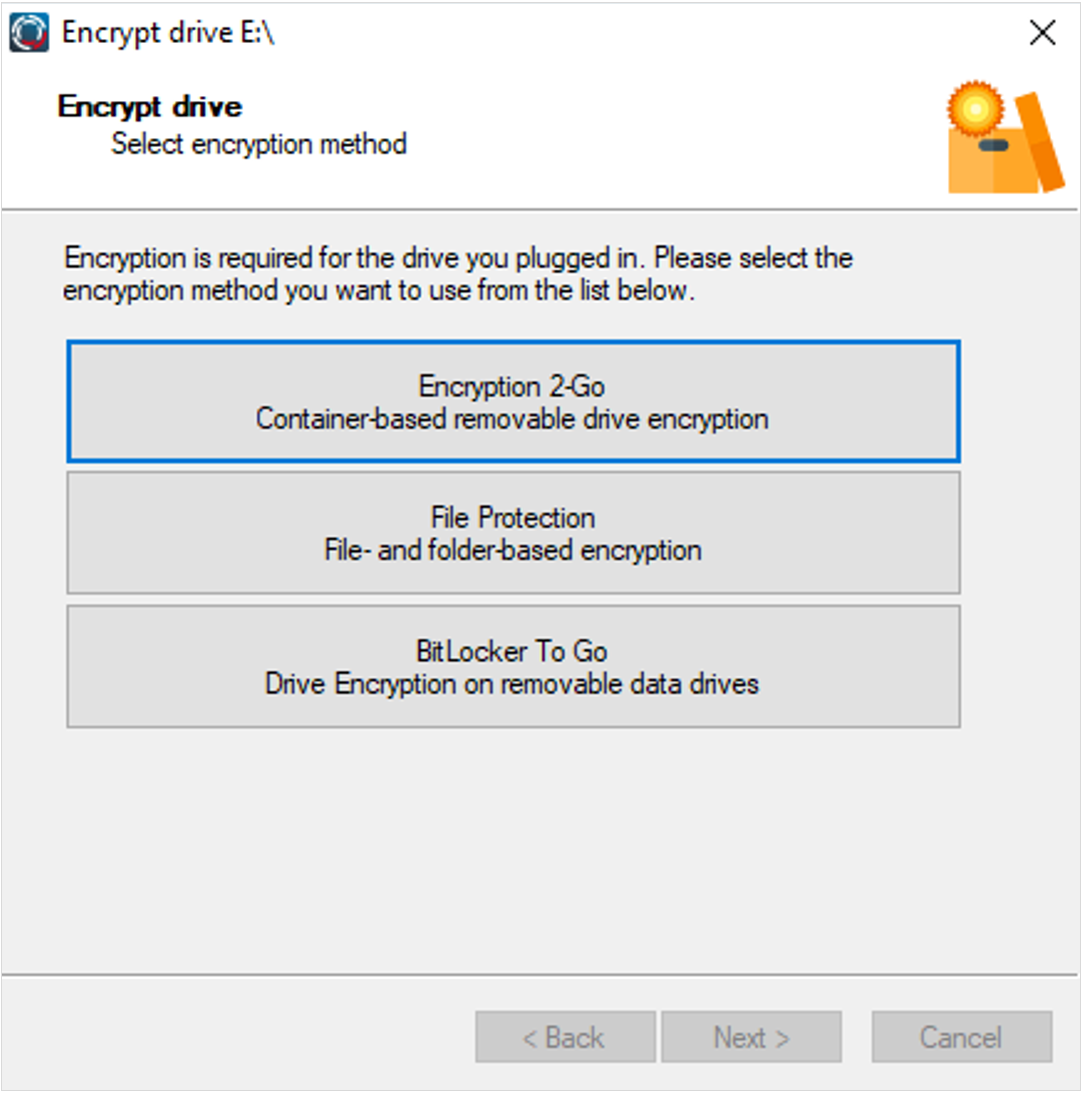
You cannot access the flash drive until it is encrypted. Once encrypted, you can unlock it either with the password set at the beginning, the administration password (e.g. here: DriveLock1), or the recovery certificate (in the DOC, in Settings > Certificates or locally in C:\ProgramData\Center Tools DriveLock\PolicyFileStg (PW: DriveLock1).
Access to the connected device is only granted after accepting the notification. Also, any data flow related to this device is monitored and tracked. If you urgently need to access a device, you can temporarlily unlock it.
Learn more about temporarily unlocking agents here.
Locked devices - BadUSB
Known BadUSB devices like USB controllers (e.g. BashBunny) and Human Interface Devices will be locked by default with the DriveLock Device Control policy.
3. How to monitoring the results in the DOC?
The DriveLock Operations Center provides you with a lot of information about your endpoints. You can, for example, use the existing Device Control dashboard, which displays graphs based on events.
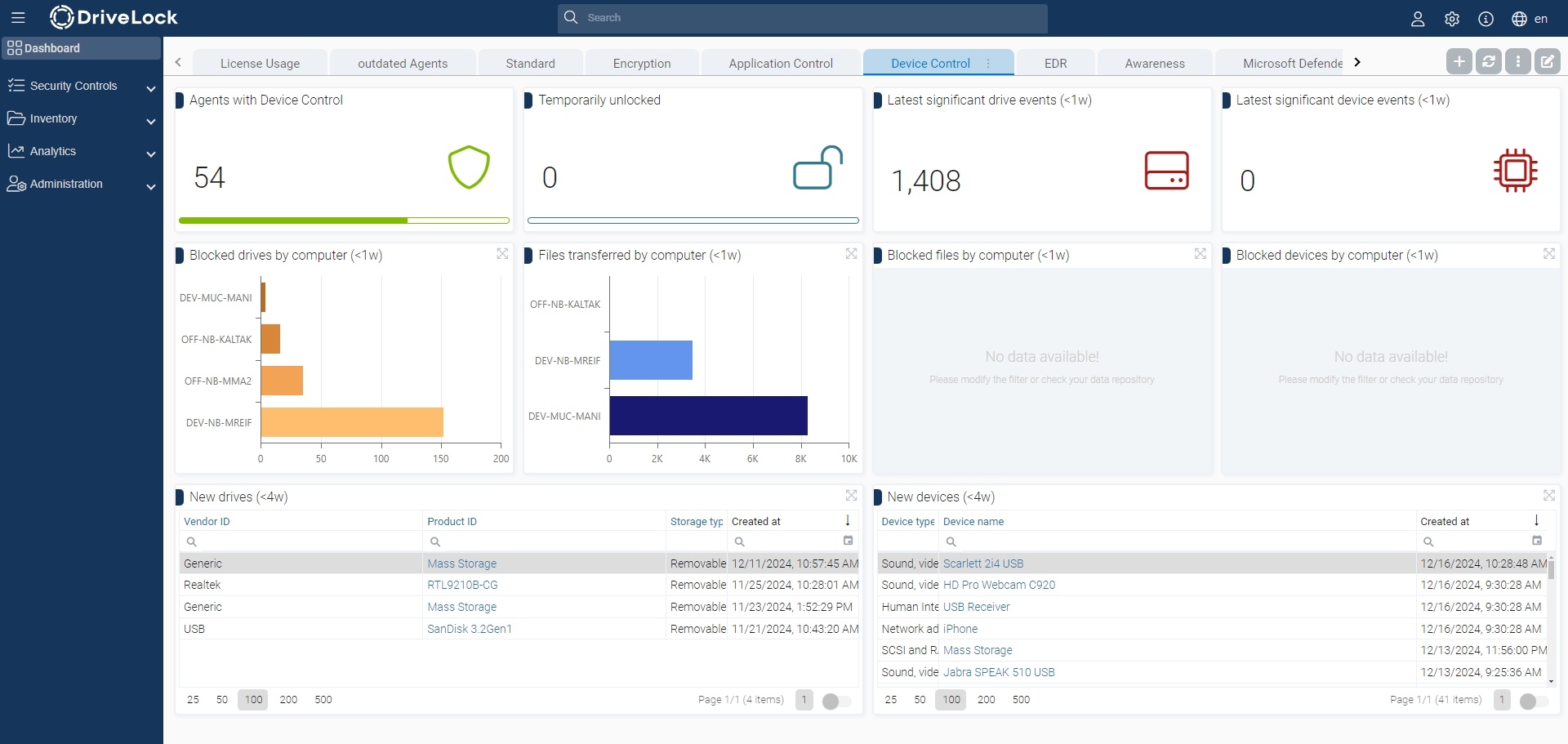
All recorded drives or devices are visible in the Security controls > Drives or Devices area. You can use the tabs in this workspace to monitor events and create and edit drive or device rules.
Instructions regarding unlock requests can be found in the following video:
In the Administration > Unlock requests area, you can view unlock requests and approve or reject open requests.
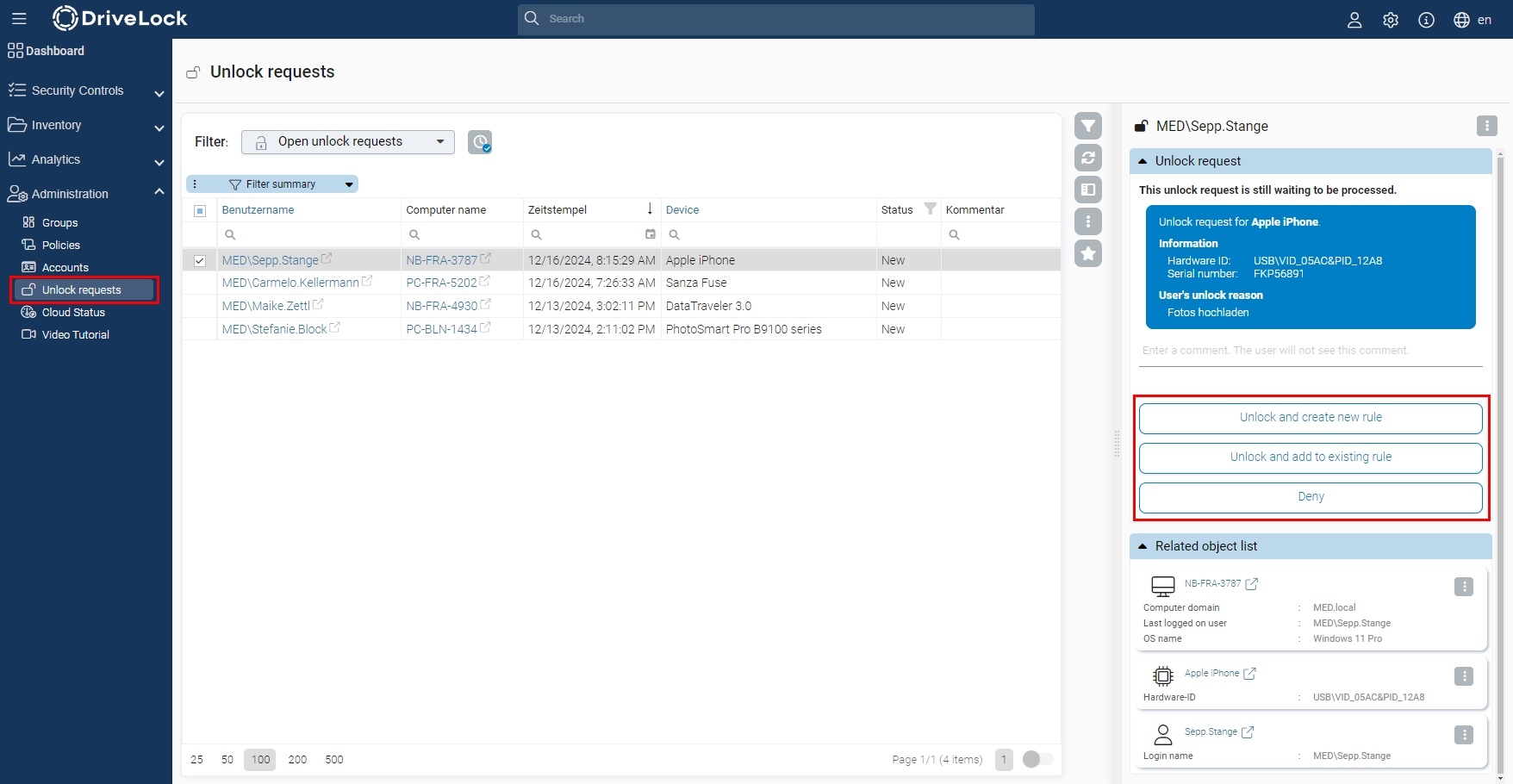
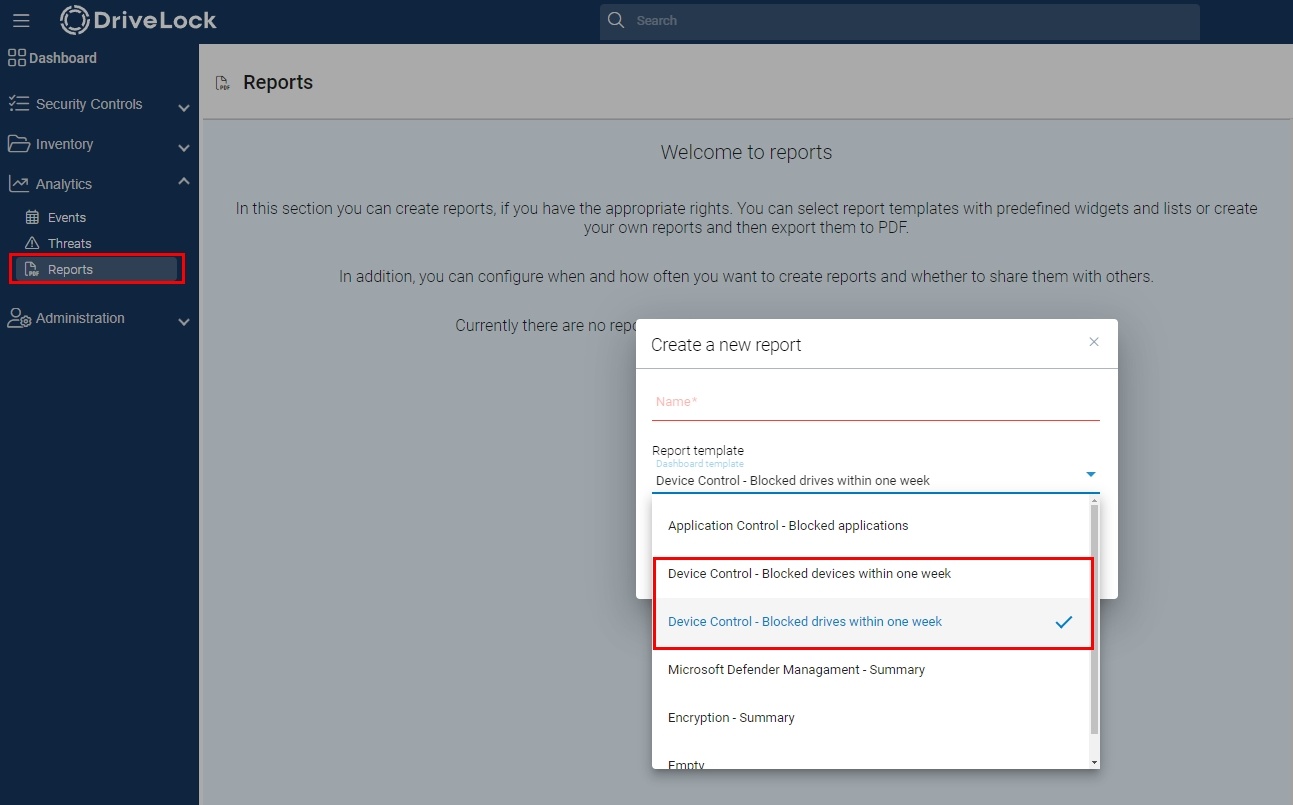
Reports can be downloaded as a PDF or sent by e-mail by defining a schedule. Notifications in the web console are also possible.