DriveLock Application Control
Start your test now!
Category: Use Case
Module: Application Control
Test time: 30 min
This use case will show you how to work with DriveLock Application Control.
1. What is the use case about?
DriveLock Aapplication Control provides forward-thinking protection against both known and unknown threats.
Ransomware or malware will no longer have a chance to disrupt your nusiness processes and destroy files or important documents. Even zero-day exploits will no longer be able to cause damage.
DriveLock protects against malware by reversing the principle of a virus scanner: Only applications that are allowed can run. Malware is blocked, no matter wether it is known or unknown.
DriveLock provides easy and automatic whitelist maintenance by offering th integrate client and patch management systems. For manual software installations, a learning mode is available.
2. How does it affect your client computer?
Once you have assigned the Activate Application Control group to a computer, the policy 20 Application Control is active on the computer. With application control, the DriveLock Agent performs an initial scan of the entire system and creates a local whitelist. After this scan, the device is sealed and only applications that are part of this whitelist can be executed.
With the application control, DriveLock provides predefined rules for blocking and allowing applications. These can be found in the Security Controls > Applications > Configuration area. If you want to allow another application, you can create your own whitelist rule. The easiest way is by right-clicking on a binary or an event of the type “473 Process blocked” in the respective tabs. In this case, the information of the executable file (certificate, path, product, version, etc.) is automatically transferred to the rule and you can customize it in the next step. You can find more information under section 4.
In addition, DriveLock creates several other rules which also include self-learning features; they do not require manual maintenance. These rules contain:
- Application rules: Blacklisting and/or whitelisting determines which applications are executed and which are blocked. In addition to special whitelist rules that allow administrators or the local system and Trusted Installer to execute applications from defined paths, there are recommended, preconfigured blacklist rules in this demo policy.
- Application behaviour rules: These determine which authorisations the applications receive, which directories applications are allowed to write to or which processes they are allowed to start. Application behaviour rules can be generated automatically by recording the application behaviour via the agent remote control. The demo policy contains a preconfigured application behavior rule for logging commandline when access is denied.
- Local learning: The DriveLock agent itself can be used to learn what is permitted by the application control.
If a user tries to run an application that is not included in any application control rule, a pop-up windows opens, informing the user that this application has been blocked.
In addition to whitelist rules, you can temporarily disable the protection of a computer via the self-service in order to install applications. The application will be added to the local whitelist on the computer.
Learn more about temporarily unlocking agents here.
3. How to monitor the results in the DOC?
For application control, there are predefined dashboard templates that give you an overview of the most important events and the status of application control on the agents.
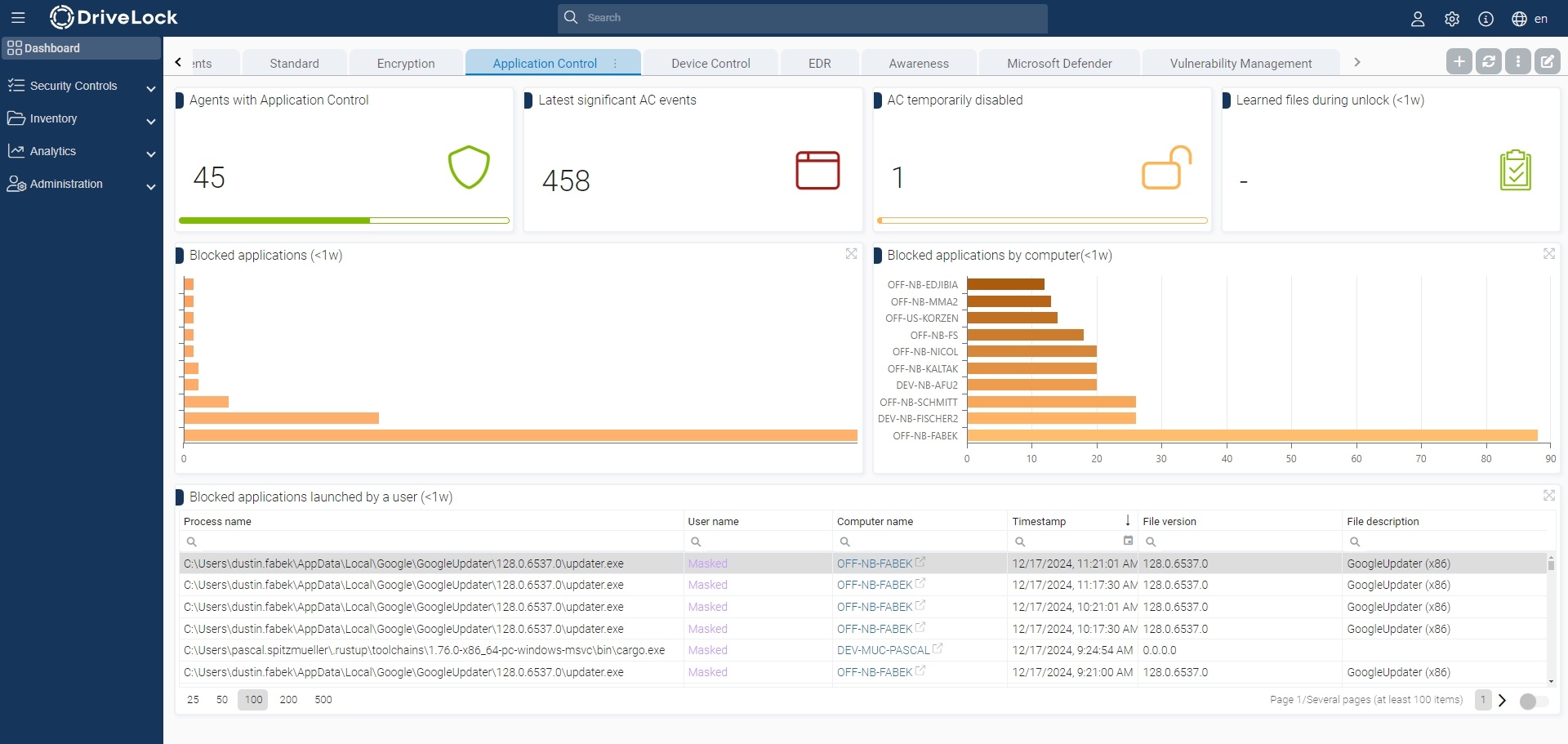
In addition to the dashboard, you can obtain detailed information about installed software, executable files and application events from the area Security Controls > Applications.
You can also add and edit your own application rules in this area in the Configuration tab (see chapter 4).
To complete the monitoring of the application control, reports can be created, for which templates are available. These can be exported and downloaded as a PDF and sent by e-mail.
4. Add more applications to the global whitelist
When an application is blocked, it generates a result with various parameters, such as file path and hash value. These parameters can then be used to create a whitelist rule for this application. This is possible with the parameters for file path and hash value, and also via the manufacturer certificates of the application.
The following video explains how to create application rules in the DOC:
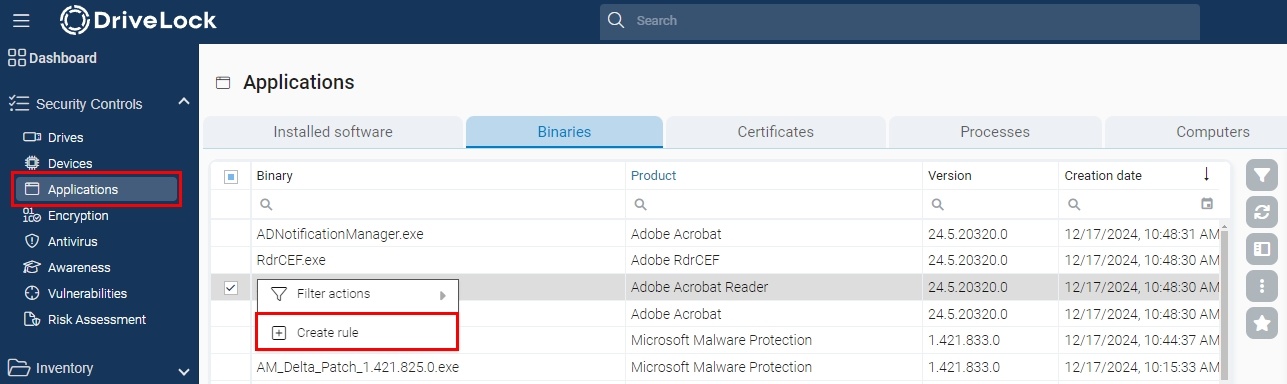
In the menu under Security Controls > Applications, go to either Installed software, Binaries or Events. There you can create an application rule by right-clicking on the blocked event, executable file or software.
Further options for creating application rules can be found under Inventory > Software or in the Analysis > Events area.
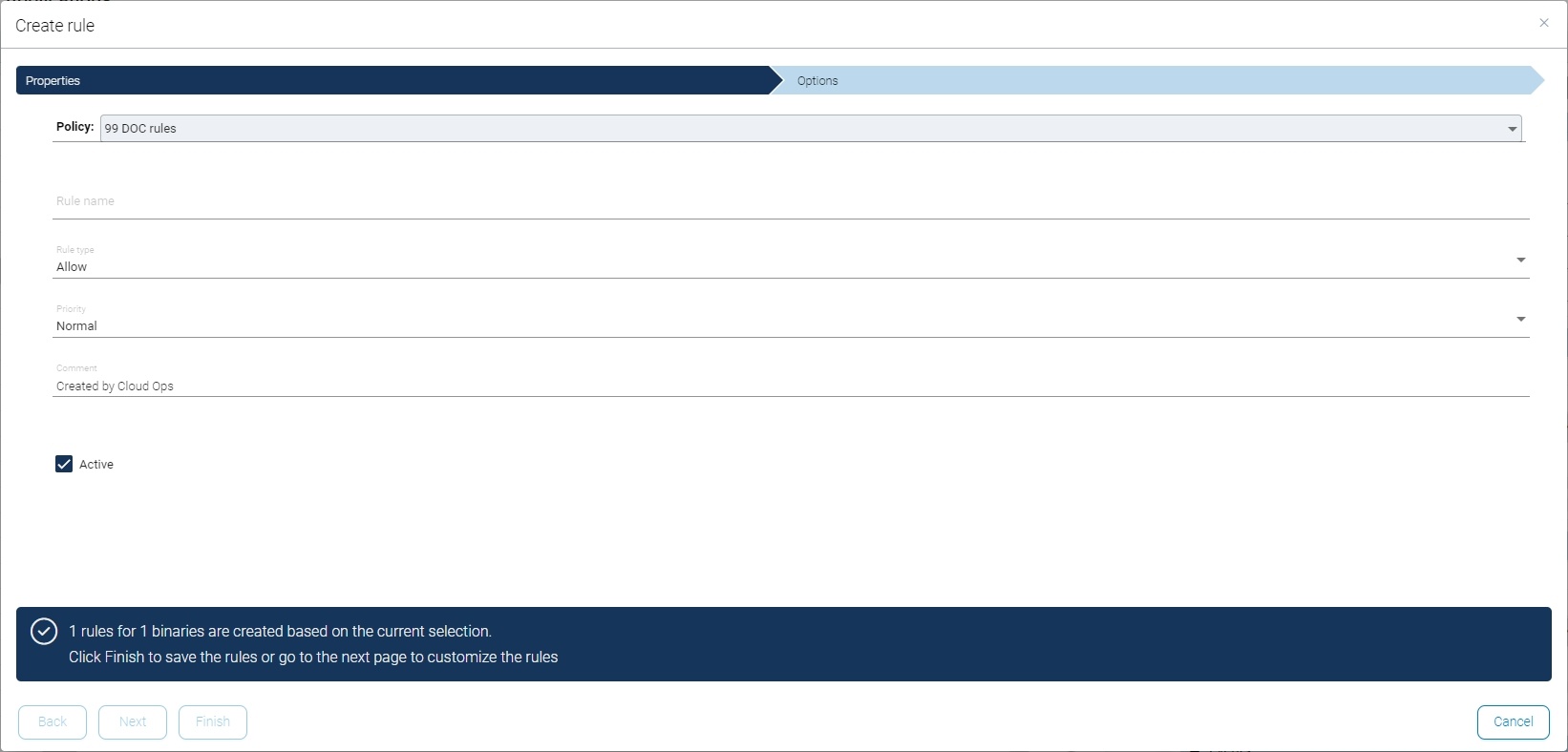
In the first step, enter a rule name and the rule type. The corresponding policy 99 DOC rules, to which the rule is added, is already preselected.
In the next step you can select and edit the parameters, which were taken over from the event or executable file.
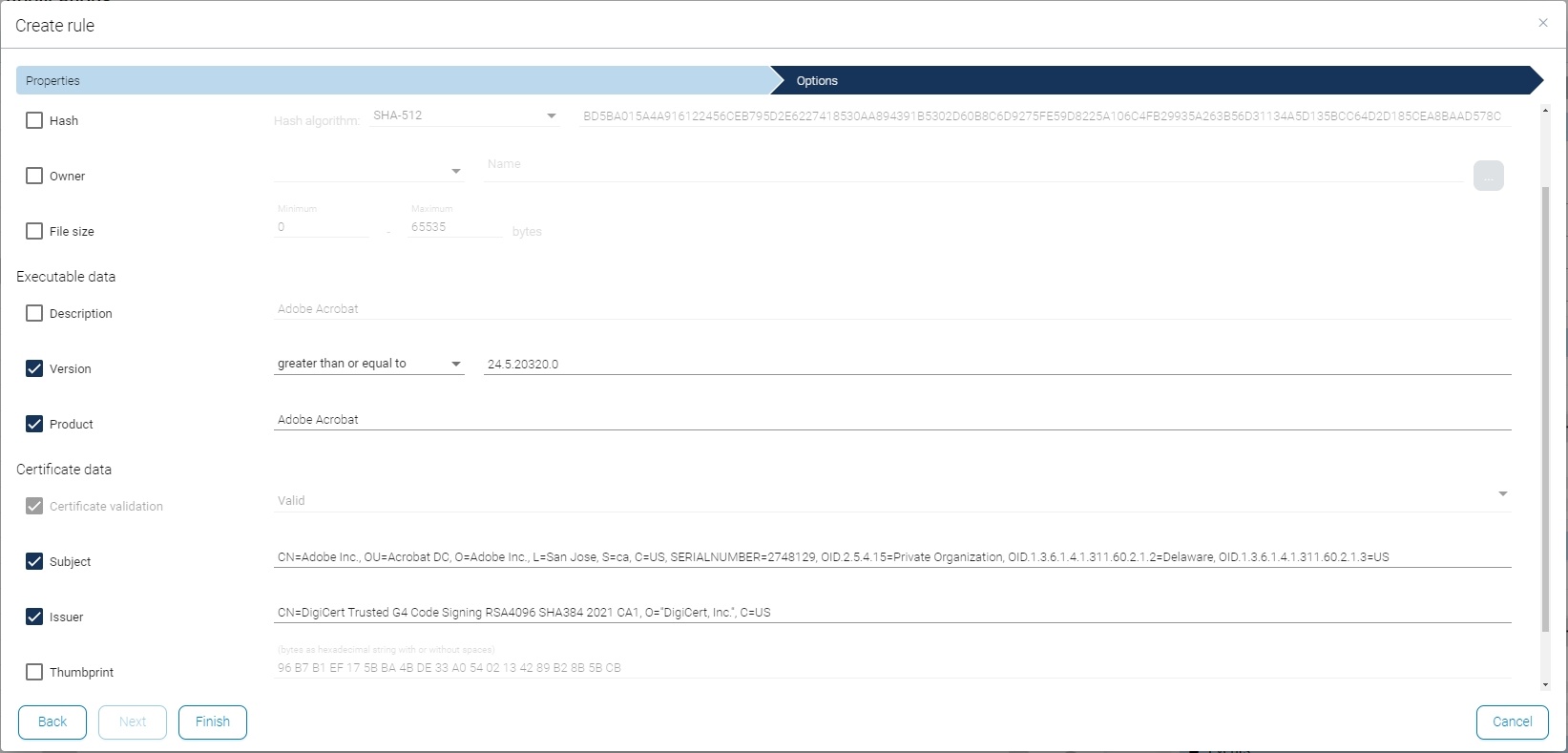
After finishing the rule, the application from this event is allowed to run according to the selected parameters (e.g. file path or certificate).


