DriveLock Bitlocker Management
Start your test now!
Category: Use Case
Module: BitLocker Management
Test time: 30 min
This use case will show you how encrypt your endpoints quickly and easily with DriveLock BitLocker Management.
1. What is the use case about?
DriveLock extends BitLocker drive encryption - The free BitLocker encryption is a great benefit for Microsoft customers and an important contribution to protecting your company's data. But only if encryption is centrally managed and consistently controlled, it can meet all legal requirements.
DriveLock adds essential and important additional features to the BitLocker functionality. Its advanced and user-friendly DriveLock Operations Center provides easy and centralized management.
CAUTION: If your computer is already BitLocker-encrypted, DriveLock will take over the encryption respectively create new protectors for recovery. The previous encryption algorithm will not be changed by this process.
2. How does it affect your client computer?
In this use case, all local hard drives are encrypted by BitLocker. Depending on the selected DriveLock group, the encryption is secured with TPM, DriveLock PBA or Microsoft PBA.
Select a preboot authentication from the following groups and assign it to your computer:
- Activate BitLocker (DriveLock PBA)
- Activate BitLocker (Microsoft PBA)
- Activate BitLocker (TPM)
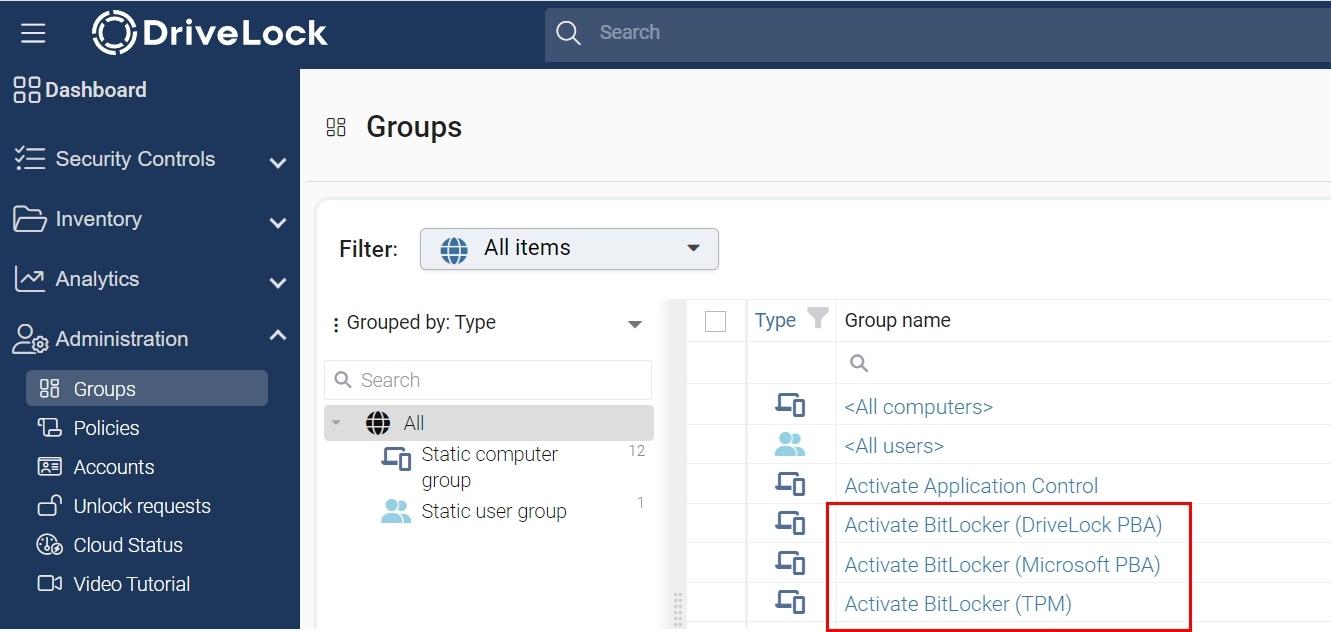
Activate BitLocker (DriveLock PBA)
DriveLock Pre-boot Authentication is automatically installed on computers with UEFI. The end user receives messages about the progress of reboots. The user logged in at the time of installation is automatically added to the PBA user database with their AD credentials.
When the user logs on to the DriveLock PBA, the Windows logon takes place automatically via single sign-on.
In addition, an emergency user is set up:
User name: RecoveryAdmin
Password: DriveLock1
Domain: Local
CAUTION: Please note that the PBA only operates on UEFI systems on Windows 10 environments and above. If BitLocker Management is used on BIOS systems, the original BitLocker PBA is used.
Activate BitLocker (Microsoft PBA)
The Microsoft PBA is used instead of the DriveLock PBA for BIOS systems.
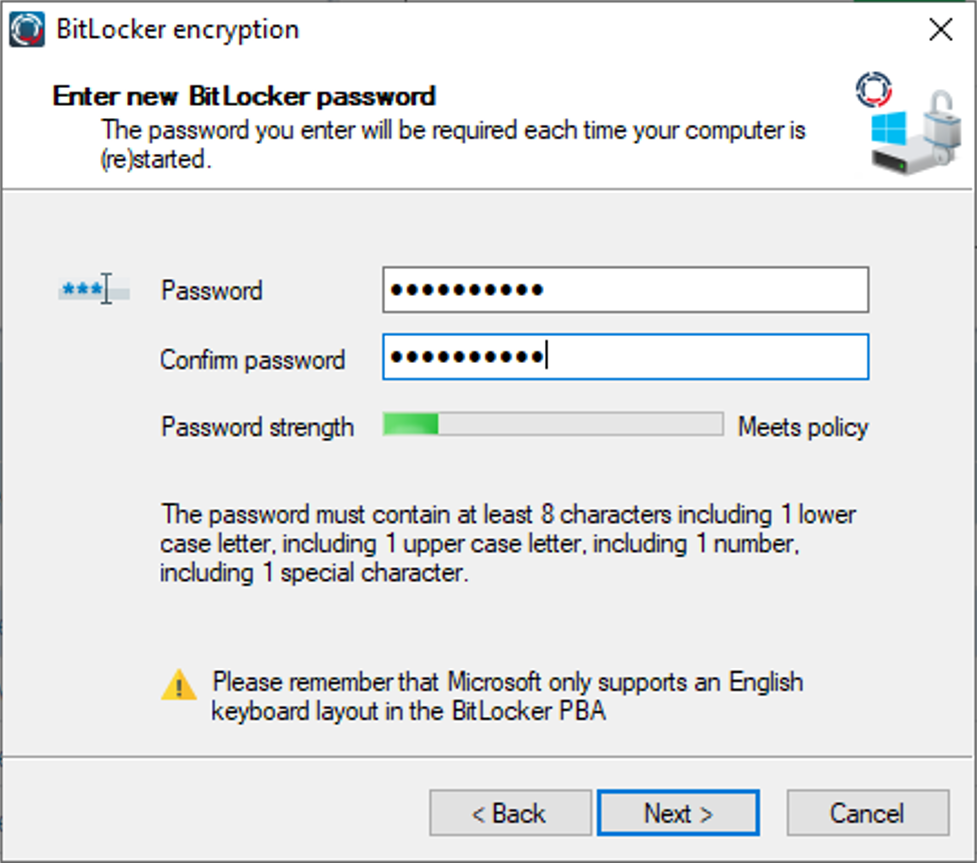
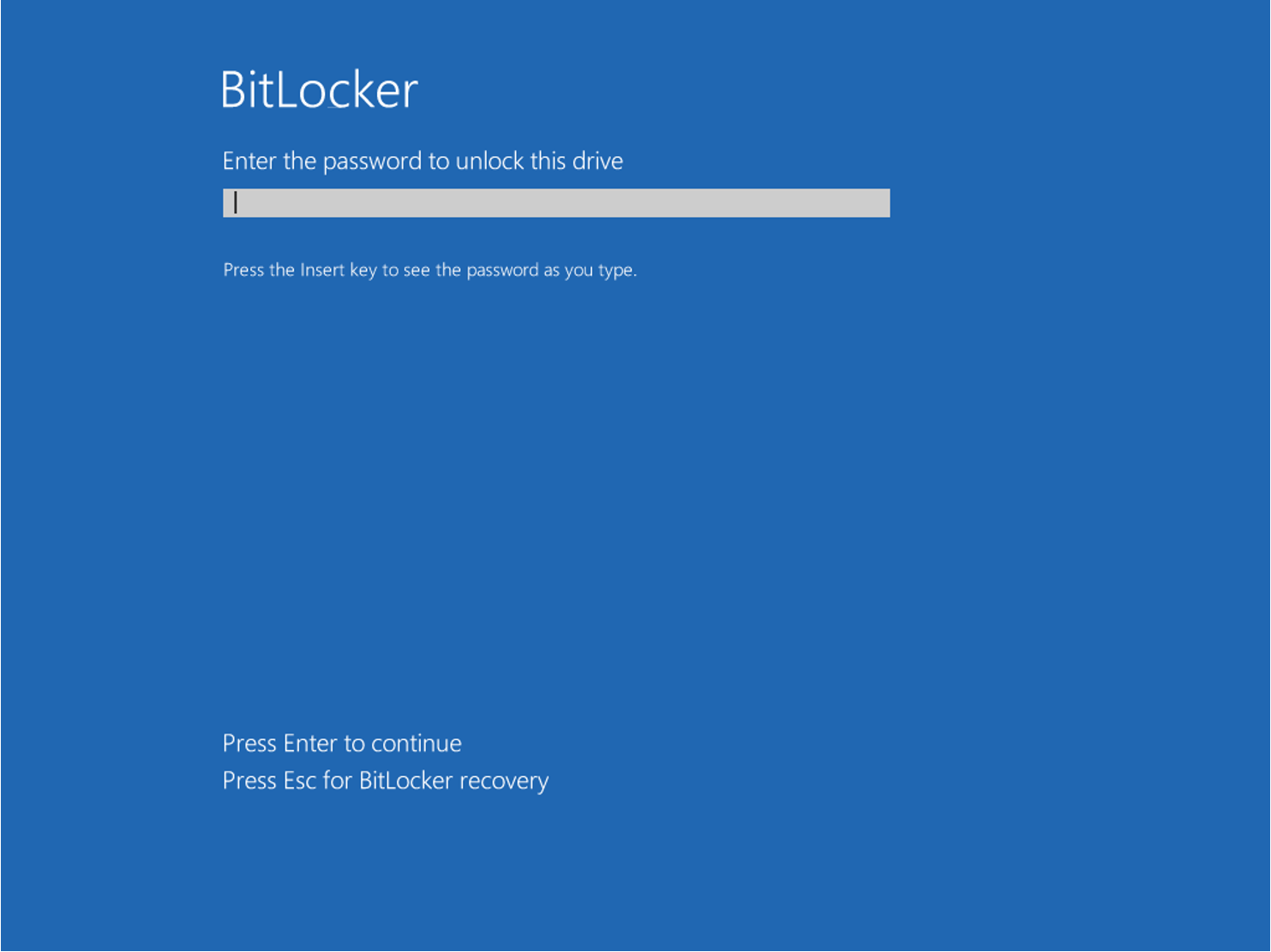
The end user is prompted to enter a BitLocker password, then encryption begins. During the encryption process, a tray icon informs you that encryption is in progress. After encryption has started, the end user will see a BitLocker PBA screen every time the test computer starts up.
Here you must enter your BitLocker password that you defined in this use case.
Activate BitLocker (TPM)
No PBA is active. An active TPM chip is required for this. Encryption starts automatically without any user interaction.
Note
All settings of the 3 different encryptions are configured in the policy 30 BitLocker Management. By assigning a group, different configuration filters are addressed within the policy.
Decryption
If you remove the computer from all Activate BitLocker (XXX) groups and the policy 30 BitLocker Management is therefore no longer assigned, the computer will be automatically decrypted.
3. How to monitor the results in the DOC?
DriveLock also offers a specific Encryption dashboard.
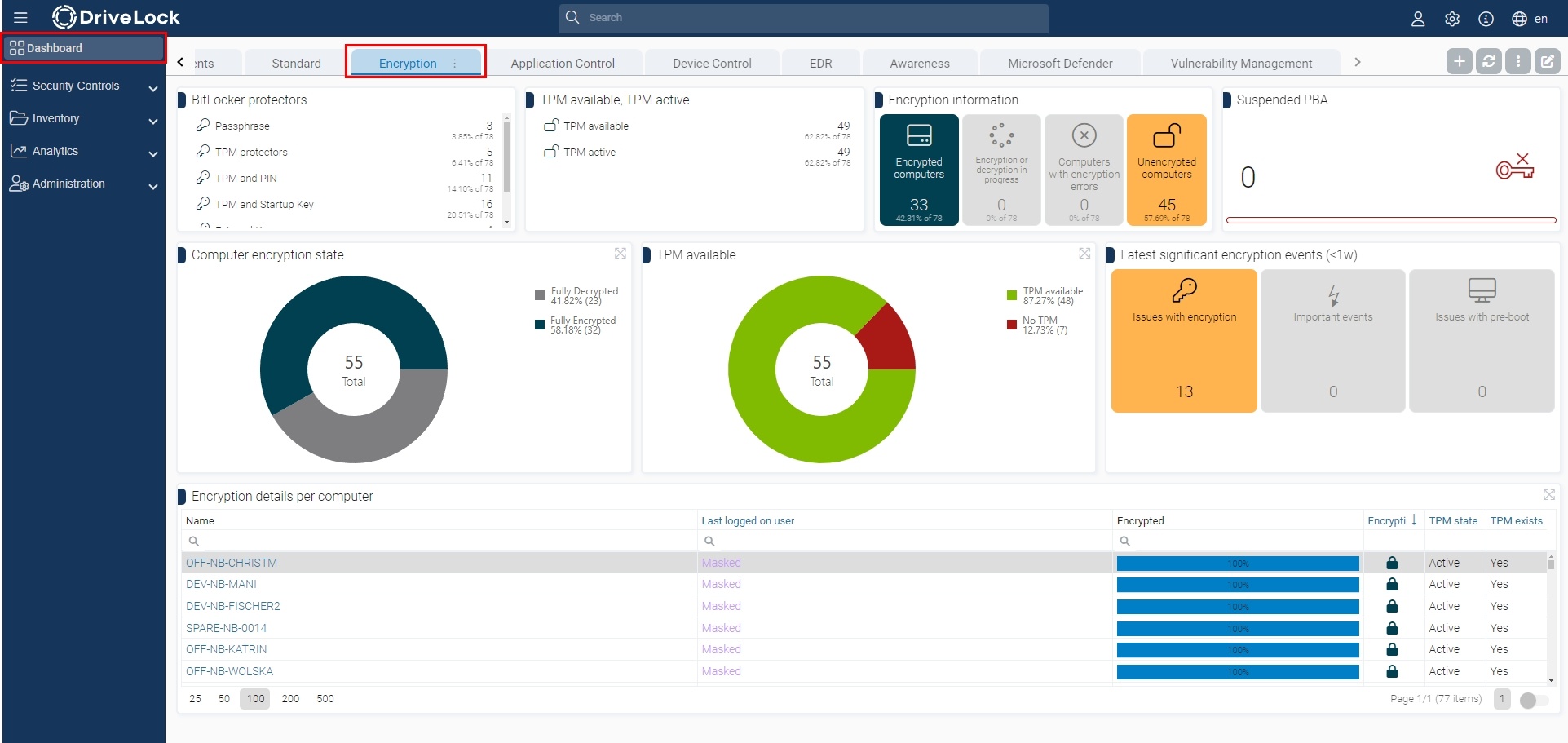
This dashboards provides you with all the information about your computers encrypted with BitLocker.
In addition, you can get more details in the view under Security Controls > Encryption or in the Computers view.
Computer-specific details for each dedicated volume are available in the Details pane on the right after you select a specific computer.
The Volumes section contains all the detailed information.
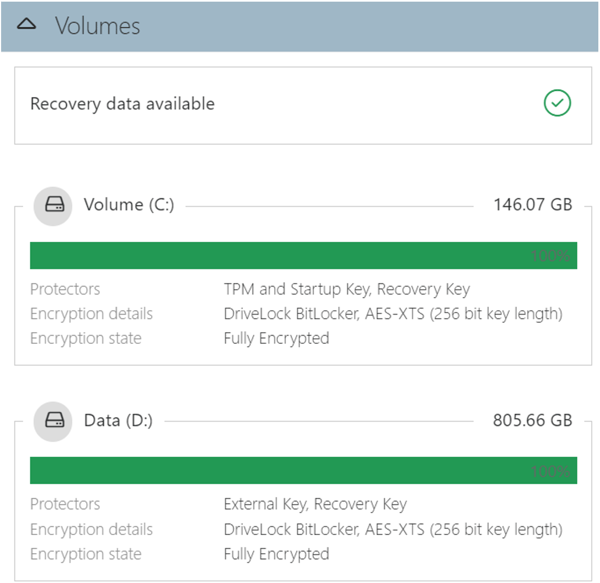
Here you can see TPM properties and all volumes including size, protectors, encryption methods and status. Also what recovery data is available for this device.
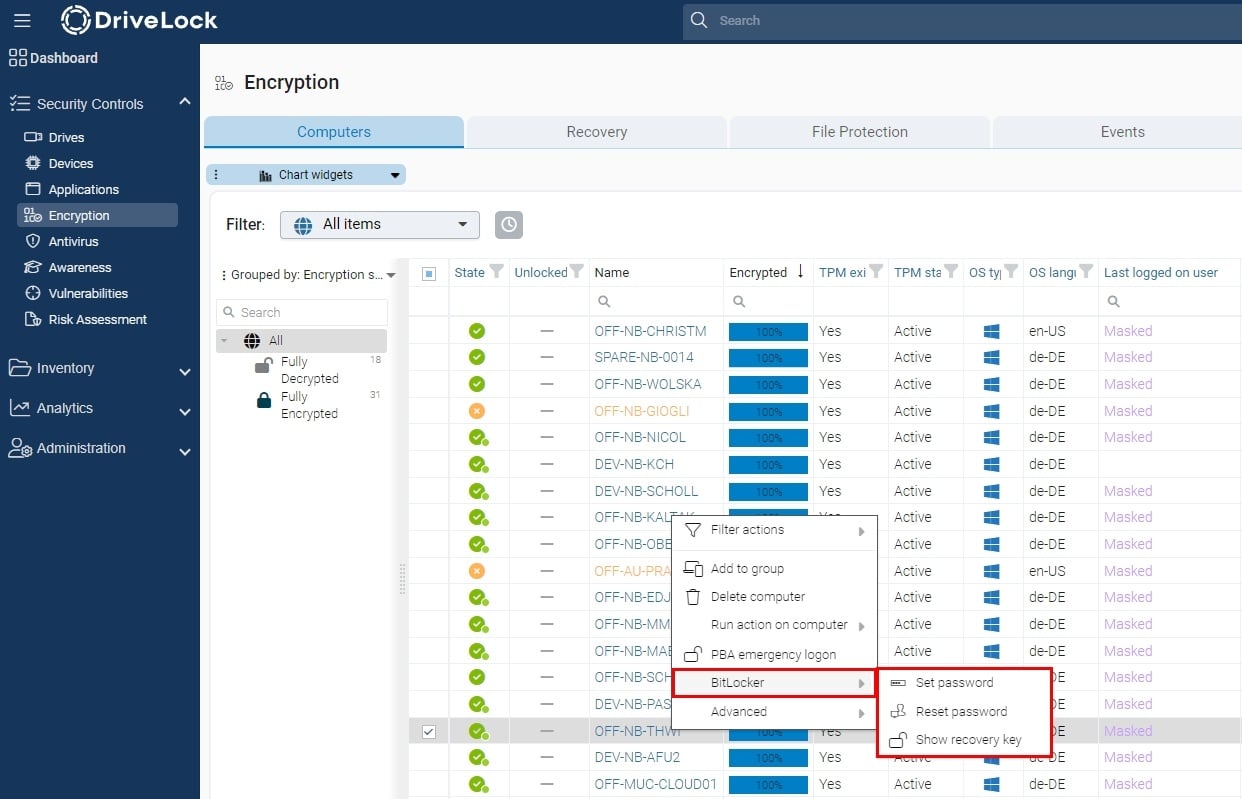
From the DOC, you can perform simple management actions regarding BitLocker, such as setting a new BitLocker password, prompting the user to reset the password, or viewing the recovery key.
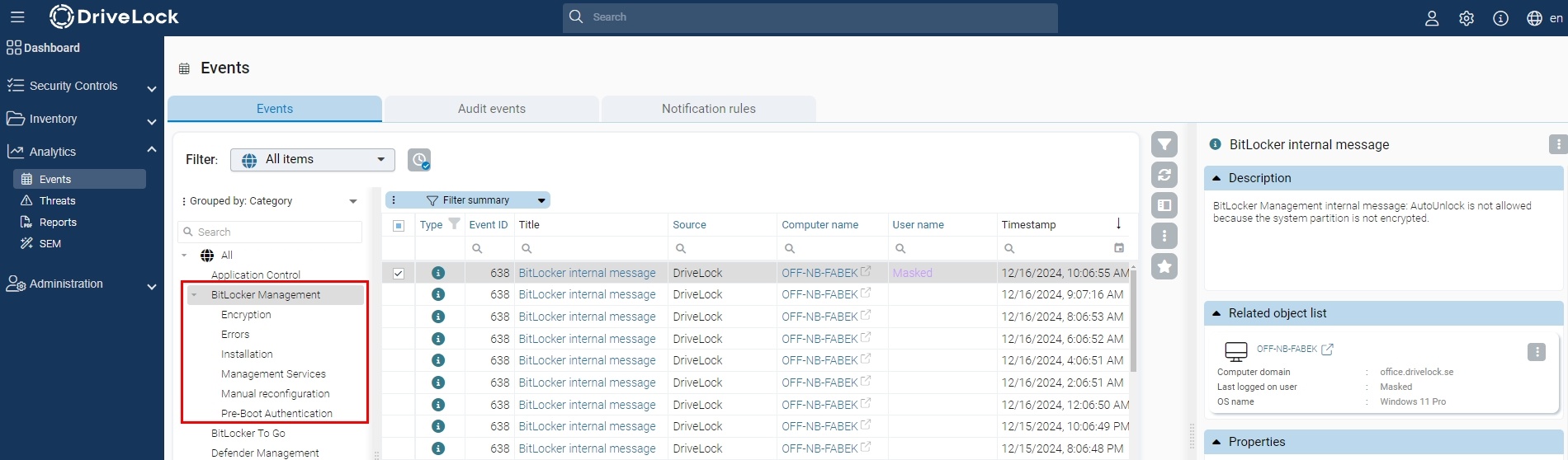
BitLocker-relevant events can be found in the tab of the same name in the Encryption view or under Analytics > Events, where you can use the predefined BitLocker Management filter.
To perform a recovery via da DOC, you will find the required BitLocker certificate DLBlDataRecovery.cer in the Settings > Certificates area or locally on an installed agent under C:\ProgramData\CenterTools DriveLock\PolicyFileStg (PW: DriveLock1)
If a recovery key is requested, you can choose the recovery data and the certificate you want to use.
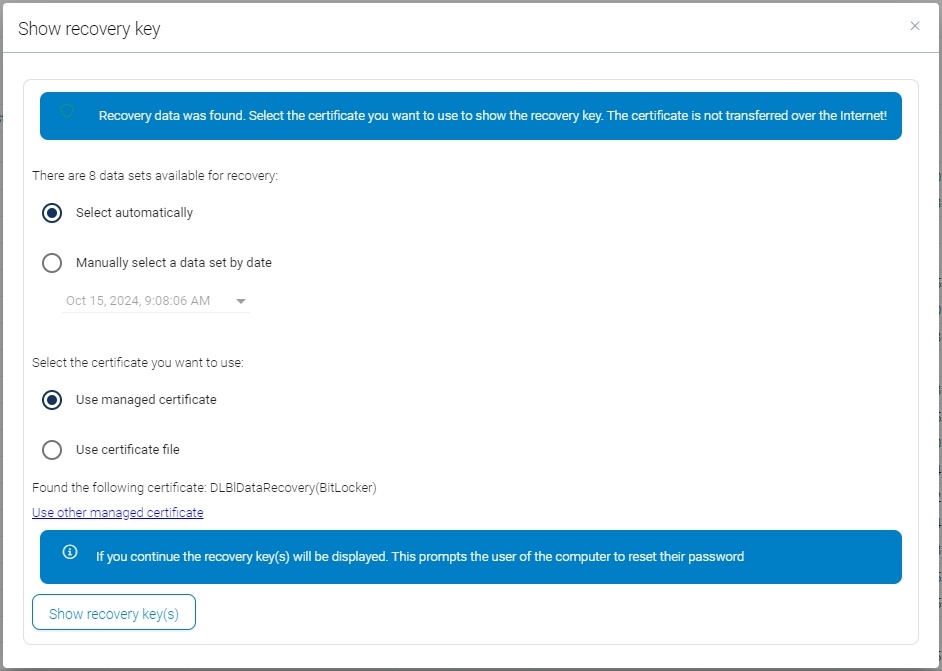
After using a recovery key, it cannot be used again. A new key is generated and uploaded to the central DriveLock service.


