Partner
DriveLock Partner und solche, die es werden wollen, kommen hier schnell ans Ziel.

DriveLock präsentiert mit HYPERSECURE IT die neue Hochleistungsklasse der IT-Sicherheit. Herkömmliche Security-Lösungen zielen darauf ab, kriminelle Machenschaften innerhalb von IT-Systemen zu bekämpfen. Wir gehen einen eigenen Weg.
Mit der HYPERSECURE Platform sorgen wir dafür, dass es Cyberangriffe erst gar nicht bis in Ihre IT hinein schaffen. Sie bleiben da, wo sie hingehören: außen vor!
Die Basis dafür: Zero Trust, next level. Made in Germany und perfekt umgesetzt.

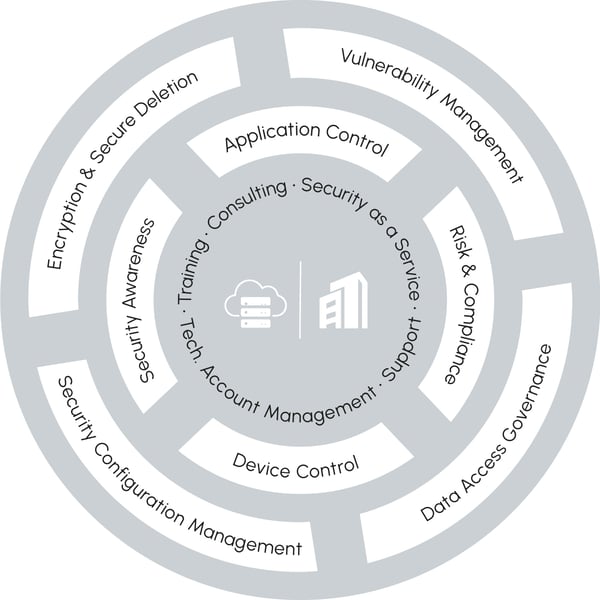
In einer Welt zunehmend intelligenter Cyberkriminalität kann alles passieren. Um so wichtiger ist ein Anti-Cyber-Attack-Konzept, das theoretisch Mögliches praktisch unmöglich macht.
Unsere HYPERSECURE Platform gleicht einer schlagkräftigen Counterforce aus hochspezialisierten Abwehrkräften, die in ihrer jeweiligen Disziplin zu den Besten zählen. Das Ergebnis ist ein Cloud-basierter Schutz des gesamten Datenlebenszyklus auf höchstem Niveau.
Technologisch führende Security Solutions nahtlos vereint zu einer effektiven Counterforce gegen Cyberattacken.
Unser einfach zu bedienender Compliance-Check liefert Ihnen eine Einschätzung Ihres aktuellen Status und Empfehlungen für notwendige Verbesserungen.
Starten Sie den ersten Schritt zur Gewährleistung Ihrer Sicherheit und Konformität Ihres Unternehmens, indem Sie noch heute unseren NIS2 Compliance Check nutzen.
Cybersicherheit ist nicht verhandelbar. Sie ist die Basis für erfolgreiche Digitalisierung in allen Schlüsselbranchen. Dazu zählen besonders Behörden, Industriebetriebe, Health Care und kritische Infrastrukturen. Eines haben alle gemeinsam: völlig unterschiedliche Anforderungen an ihre IT-Sicherheit.
DriveLock entwickelt seit Jahrzehnten maßgeschneiderte Lösungen für systemrelevante Branchen. Im engen Schulterschluss mit führenden Anwendern und Partnern aus der Praxis für die Praxis.
Cybersicherheit ist nicht verhandelbar. Sie ist die Basis für erfolgreiche Digitalisierung in allen Schlüsselbranchen. Dazu zählen besonders Behörden, Industriebetriebe, Health Care und kritische Infrastrukturen. Eines haben alle gemeinsam: völlig unterschiedliche Anforderungen an ihre IT-Sicherheit.
DriveLock entwickelt seit Jahrzehnten maßgeschneiderte Lösungen für systemrelevante Branchen. Im engen Schulterschluss mit führenden Anwendern und Partnern aus der Praxis für die Praxis.
DriveLock Partner und solche, die es werden wollen, kommen hier schnell ans Ziel.
DriveLock Kunden und Interessierte finden hier nützlichen Informationen auf einen Blick.
Anfragen, Nachfragen, Rückfragen? Persönlich, schriftlich, freundlich ... hier entlang!
DriveLock Partner beherrschen ihr Business – und das ihrer Kunden. Warum? Weil sie IT-Sicherheit im Blut haben und die Anforderungen unterschiedlicher Branchen im Detail kennen. Unsere Experten verstehen sich mit ihrem jeweiligen Fokus als Teil eines starken Partner-Netzwerkes ausgewiesener Sicherheitsspezialisten.
Erfahren, umsetzungsstark und pragmatisch nutzen unsere Partner auch komplexe Herausforderungen als Chance, mit HYPERSECURE IT Best-in-Class-Resultate zu erzielen.

Das DriveLock Partnernetzwerk steht für herausragendes Spezial-Know-how im Bereich komplexer IT-Security-Anforderungen.
DriveLock bietet Ihnen einen umfassenden Security-Service - vom Hosting der kompletten Lösung bis zur Verwaltung durch erfahrene IT-Security-Experten.
DriveLock bietet Ihnen höchste IT-Sicherheit bei maximaler Skalierbarkeit. Sicherheitsstandards sind individuell anpassbar sowie ressourcenschonend je nach Schutzbedürfnis, Unternehmensgröße und -wachstum.
Sie erhalten einen hohen Standard administrativer und technischer Sicherheitsmaßnahmen: BSI-auditierte Microsoft Cloud Services, Cloud Computing Compliance Controls Catalogue (C5) und Common Criteria EAL 3+.
Das Security Management wird exakt an Ihren Anforderungen ausgerichtet - mit individuellen Firmen-Sicherheitsrichtlinien oder der Verwaltung und Konfiguration der Sicherheitsprofile.
DriveLock und Microsoft Azure Cloud gewährleisten die Vertraulichkeit, Integrität und Hochverfügbarkeit Ihrer Daten.
DriveLock gewährleistet weltweit maximale IT-Sicherheit durch Rechenzentren mit hochverfügbarer Infrastruktur in Europa, Support in Deutschland und garantiert keinem Backdoor.
Verhindern Sie mit Application Whitelisting die Ausführung unbekannter und unerwünschter Programme.
Mehr erfahrenSchärfen Sie das Sicherheitsbewusstsein Ihrer Mitarbeiter und reduzieren Sie Ihr Security-Risiko.
Zentralisieren und automatisieren Sie die Verschlüsselung Ihrer Festplatten und überwachen Sie den Compliance-Status.
Verwalten Sie Microsoft Defender Antivirus komfortabel gemeinsam mit unseren Präventionswerkzeugen.
Überzeugen Sie sich selbst. Testen Sie die Einsatzszenarien, die für Ihr Unternehmen von Bedeutung sind.
Heute testen - morgen HYPERSECURE!

Unser Ziel war es, das Risiko eines Datendiebstahls durch nicht gesicherte USB-Ports an den PCs auf unseren Verkaufsflächen zu verhindern. Dank DriveLock konnten wir dieses Ziel schnell umsetzen.
Wir sind sehr zufrieden mit der Lösung von DriveLock. Diese funktioniert einwandfrei und ist so flexibel, dass sie uns zahlreiche Ausbaumöglichkeiten bietet. Auch für neue Anforderungen an die IT-Sicherheit sind wir mit DriveLock sehr gut aufgestellt.
Das Application-Control-Modul von DriveLock hat unsere Verwaltung bereits mehr als einmal wirksam vor Ransomware und den damit einhergehenden, schwerwiegenden Konsequenzen geschützt.
Dank DriveLock haben wir unsere Geräte abgesichert und sind damit für die Zukunft gut aufgestellt. Die Einrichtung hat durch die Hilfe von DriveLock reibungslos funktioniert.








.png?width=500&height=200&name=DsiN%20Mitglied%20%20(500%20x%20200%20px).png)




